Checklist for initial configuration of the protection policy
List of steps
Details
1. Make sure the routing rules for the policy are set.
Make sure that the routing rules are set for the policy
on the “Policy Setup” tab of the “Protection policy” page.
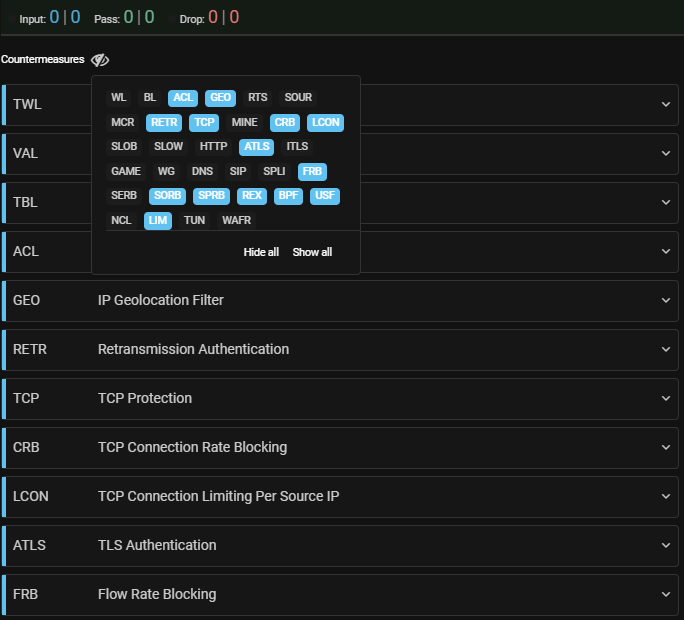
2. Configure the policy to display only the necessary countermeasures.
You can hide countermeasures not used in the policy by clicking on the icon
above the list of countermeasures. The “Hide all” button disables the display of all countermeasures
of the policy other than the active ones (countermeasure enabled, learning enabled,
autodetection enabled).
3. Set up countermeasures.
The principle of operation of countermeasures is described in the built-in help. The parameter values
are set based on the specifics of the protected service and the parameters of the traffic passing
through the policy.
4. Set up automatic packet capture.
Set automatic packet capture settings on the “Packet capture” tab
of the protection policy. In the event of an attack, the mechanism will automatically dump traffic
according to the specified parameters and send it to the specified email.
5. Set up autodetection
Set auto-detection settings on the “Autodetection” tab of the protection
policy.
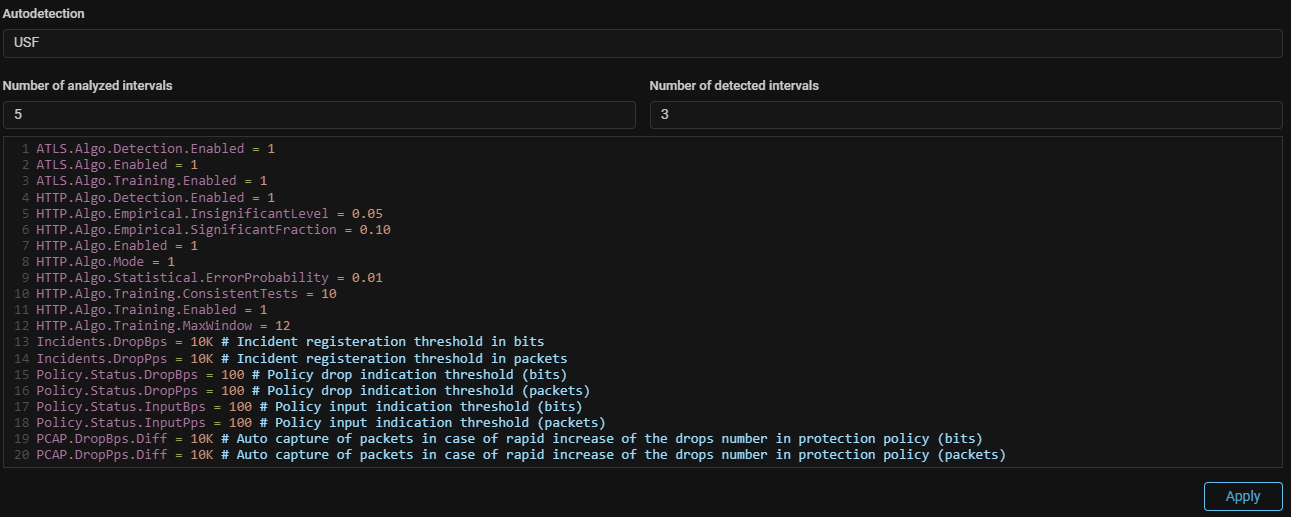
-
Set the automatic activation and deactivation parameters for each of the countermeasures, which assumed to be activated by the autodetection mechanism.
-
Set the
Policy.Status.thresholds to change the indication in the policy. -
Set the
Incidents.thresholds, above which an incident is registered in the system. It is recommended not to set zero values for these thresholds, so that small sporadic drops would not reported as incidents. -
Set the
PCAP.thresholds above which the automatic packet capture mechanism will be activated.
6. (Optional) Check the effect on legitimate traffic via the test mode.
Activate the protection policy test mode on the “Policy settings”" tab
and make sure that the countermeasures settings are correct according to their graphs.
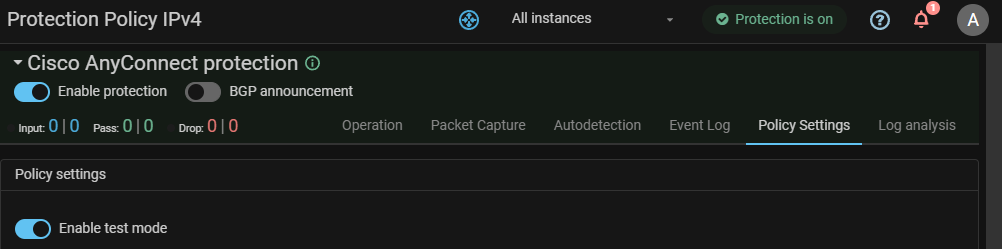
7. Enable protection policy.
Activate the “Enable protection” switch in the upper left corner of the policy page.
8. (Optional) Configure the log analyzer.
If log delivery of the protected Web servers is configured via syslog,
it is necessary to set the rules that form the criteria for detecting anomalies in the logs
of the protected server. The rules are set on the “Log Analysis” tab of the protection policy.
The rules syntax is described in the in-built help.
9. (Optional) Pin countermeasure graphs
It may be convenient to pin graphs of countermeasures under the general graph on the right side of the
policy page. Pinning is done by clicking on the pin icon in the countermeasure
header.