Version v23.08
v23.08 added connection monitoring, support for ISN synchronization for anycast
IP addresses, configuring the log retention time, the ability to always mark
traffic from IP addresses in HPD, sending sFlow on dropped traffic, displaying
both units of measurement simultaneously on policy graphs, and general protection.
Enhanced functionality of countermeasures SCAN, WL, WL6, TCP, MINE, HCA, VAL, DNS,
ATLS, DTLS, JA3, SPLI and also autodetect mechanism and Logan.
Changes in v23.08.1
Notifications. Added custom subject prefix for email notifications.
Now you can set a prefix that will be inserted into the subject of notification emails.
Reports. A summary of blocked IP addresses has been added to the incident report.
The report now displays information about the number of blocks by individual countermeasures and in total, as well as the number of unique blocked IP addresses.
Stats. Added sending of blocking reasons logs for ATLS and DTLS countermeasures to the analytics server.
Changes in v23.08
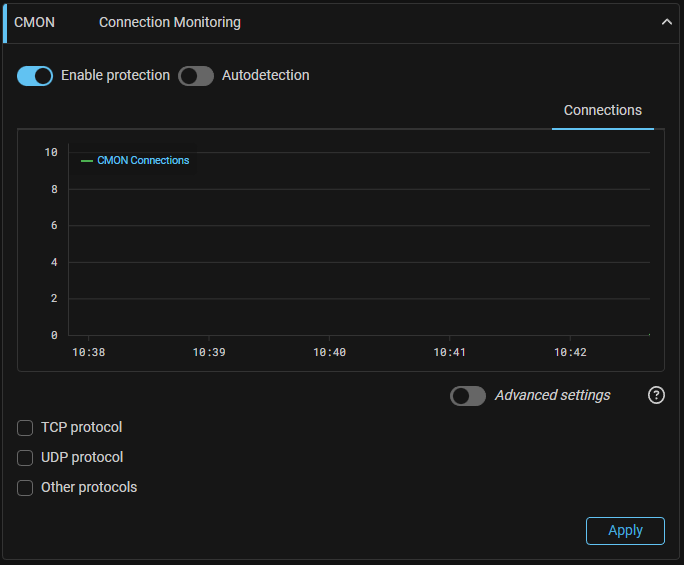
CMON. Added a new function "Connection Monitoring".
The functionality is needed so that countermeasures do not break established connections when enabled. The mechanism is similar to learning in TCP, MINE, USF countermeasures.
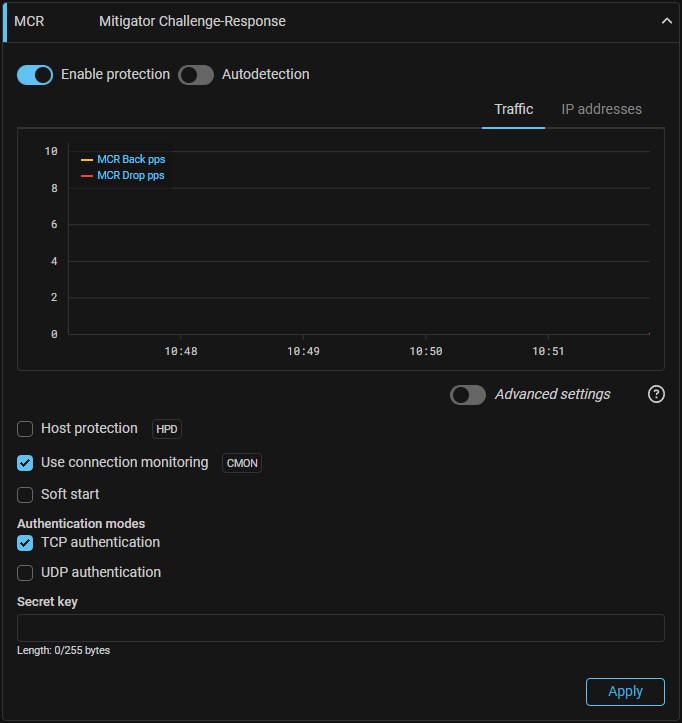
MCR. Added the "Connection Monitoring" function usage.
WL. The principle of prefixes decomposition when saving the list has been changed.
After adding the per-countermeasure bypass functionality, prefixes began to decompose in /32. Now when you save the list, prefixes only decomposed if they are:
- prefixes with /29 to /31 mask;
- prefixes for which bypass countermeasures are specified.
This avoids WL overflow.
WL6. The principle of prefixes decomposition when saving the list has been changed.
WL. The ability to pass a packet without processing by countermeasures that work after protection policies has been added to general protection.
Bypass for countermeasures DLIM, PLIM, TLIM, SCAN, and LACL can now
be specified in the IPv4 General Protection WL.
WL6. The ability to pass a packet without processing by countermeasures that work after protection policies has been added to general protection.
Bypass for countermeasures PLIM and LACL6 can now be specified in the IPv6
General Protection WL.
SCAN. Traffic pass to specific dst ip has been added.
Now you can specify the IP addresses the countermeasure will pass traffic to without processing.
HPD. Added the ability to always mark traffic from IP addresses.
Now, in the countermeasure, you can specify prefixes, traffic from which is always marked as to be processed. This allows to process traffic from suspicious senders even if the host protection thresholds are not exceeded. Named lists are supported.
VAL. Management of optional packets drop criteria by the autodetect mechanism has been added.
Added the ability to manage the state of additional validation criteria using the auto-detection mechanism. Each of the additional validation criteria in the countermeasure can be permanently enabled, permanently disabled, or controlled by the autodetection mechanism. This corresponds to the “On”, “Off” and “Auto” buttons.
VAL. Changed optional packets drop criteria.
Now drops for TCP SYN without options and TCP SYN+ACK without options are enabled separately.
TCP. Added learning mechanism support when using HPD.
Now, when learning is enabled, the countermeasure takes into account IP addresses for which there is no excess in HPD.
MINE. Added learning mechanism support when using HPD.
HCA. Added learning mechanism support when using HPD.
ATLS. Added support for fragmented IP packets.
Now the entire ClientHello message contained in several IP fragments collected by FRAG is parsed, and not just the first fragment.
DTLS. Added support for fragmented IP packets.
JA3. Added support for fragmented IP packets.
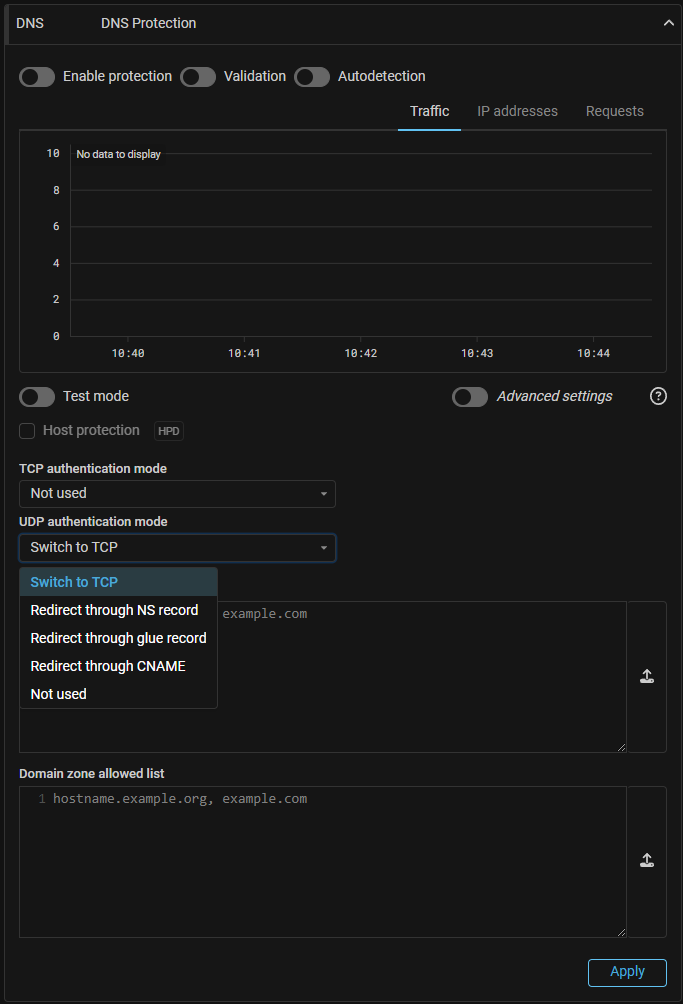
DNS. Added new UDP authentication mode.
Added new UDP authentication mode via CNAME.
SPLI. Added connection mode with delayed data sending.
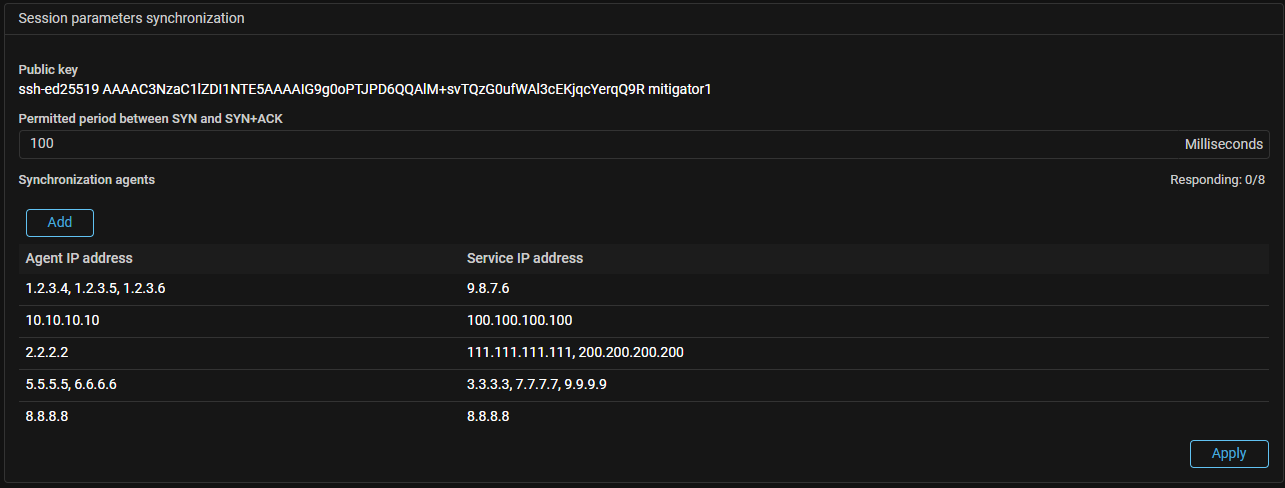
ISN agent. Added support for ISN parameter synchronization scenario for anycast IP addresses.
It is used for cases when several servers are responsible for one IP address. You need to update the synchronization agent and set a match between the IP addresses of the services and the IP addresses of the synchronization agents installed on the servers of these services in policy settings.
LOGAN. Added flag for rule applicability only to Web server logs with a specific token.
For cases when the logs of several Web servers with different tokens are received
in the protection policy, the for keyword has been added, which allows you to
specify a token in the rule.
The rule in this case will only apply to the web server logs with the specified
token.
Example:
block 400 src.uniq.uri limit 100 period 10 for 1234567891287654This rule will block for 400 seconds the IP address who send more then 100 requests
with different URIs in 10 seconds to the web server with 1234567891287654 token.
If you want a rule to apply to the logs of several Web servers, but not to all, you should write the same rule several times with different token values.
LOGAN. Added the ability to set the domain name as a token.
Now you can specify a domain name as a token. This may be required if the logs of several web resources come from the same source, for example, WAF.
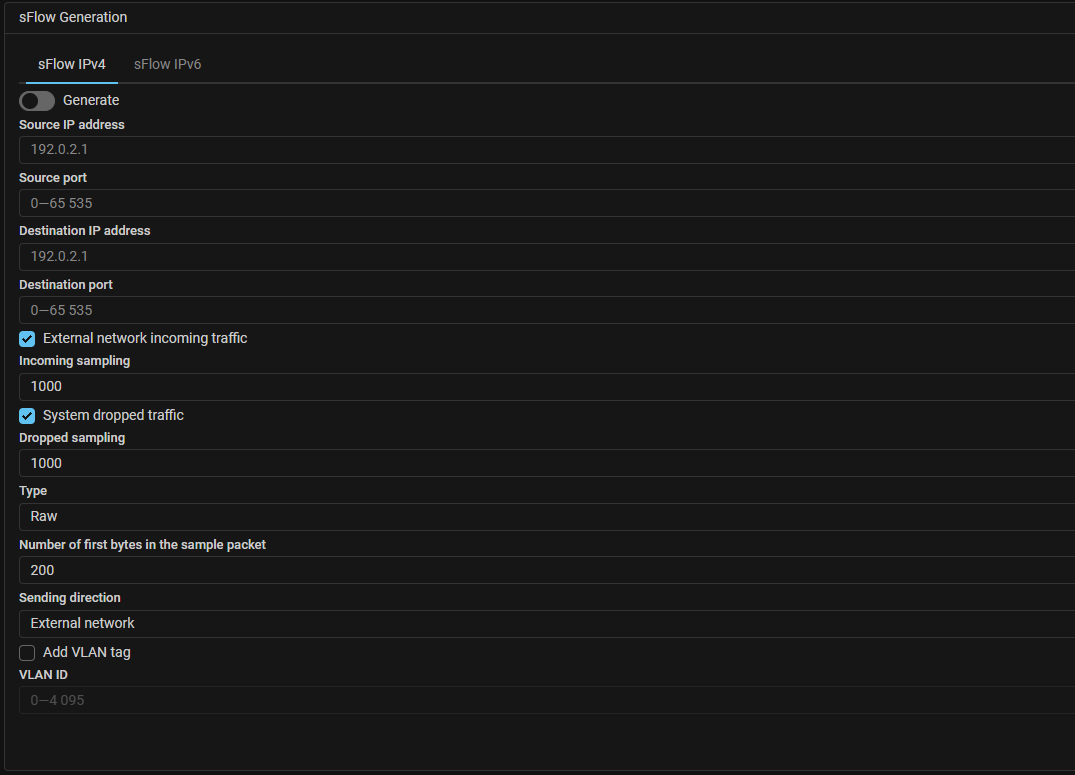
sFlow. Added sending sflow on dropped traffic.
Now in MITIGATOR you can independently collect and send sflow on incoming traffic from the external network and on traffic dropped by countermeasures.
This allows more detailed analysis and visualization of traffic dropped by countermeasures.
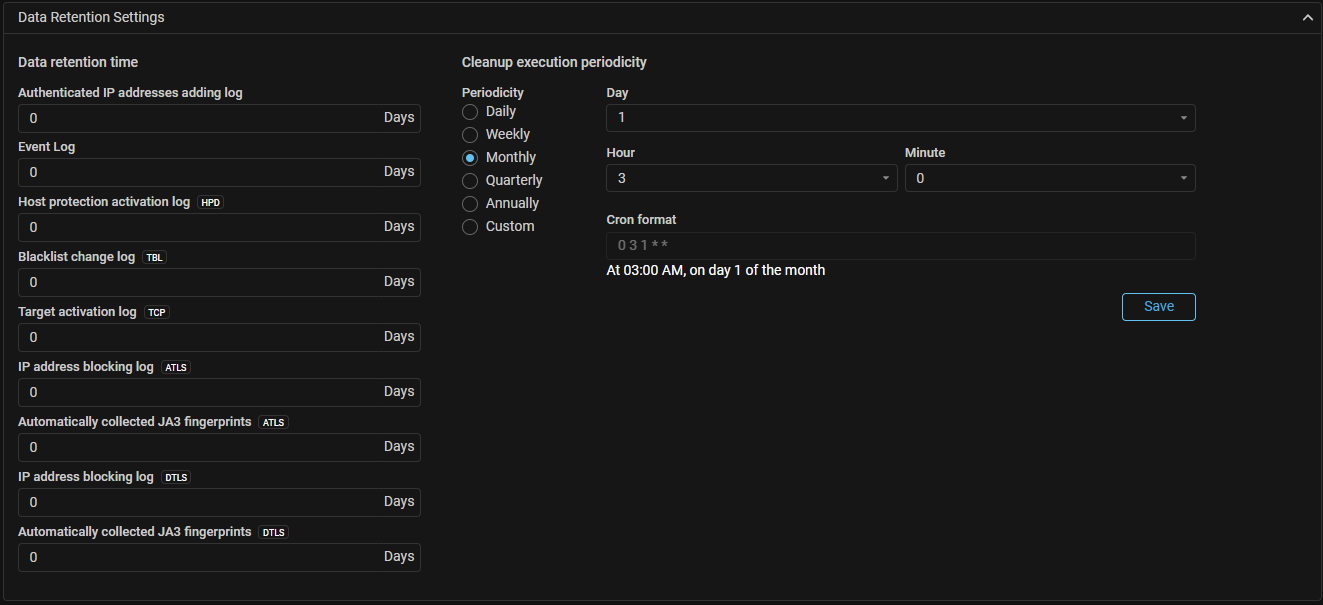
Journals. Added setting for log storage depth.
The mechanism deletes records older than the specified retention time from the system at a specified interval. The retention time for different data is set independently.
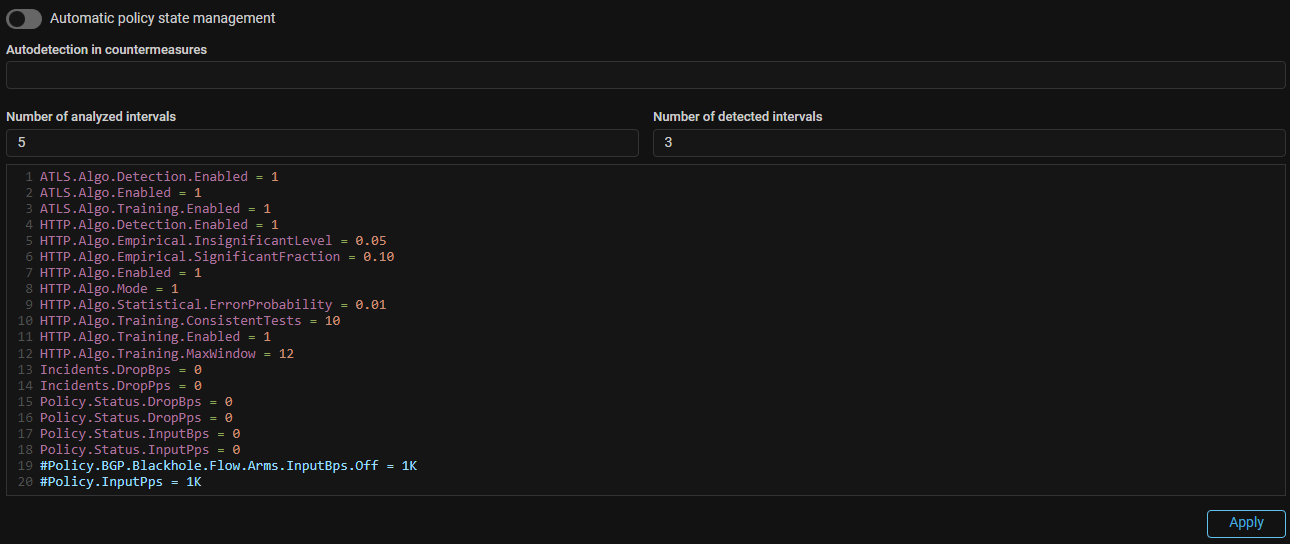
Detect. Added thresholds for holding a countermeasure state by the drop counters of another countermeasure.
Now you can set autodetect thresholds for countermeasures of the form
<element1>.Drop.<element2>.{Pps,Bps}.{On,Off}, where <element1> is a countermeasure
controlled by the threshold, <element2> is a countermeasure that triggers the threshold.
<element1> and <element2> can be the same.
Examples:
- The
GEO.Drop.GEO.Pps.Off = 100threshold means that the GEO countermeasure will not be turned off as long as it has a drop greater than 100 pps. This can be useful if the countermeasure is turned on by passed traffic metric. - The
ACL.Drop.BL.Pps.Off = 100threshold means that the ACL countermeasure will not be turned off as long as the BL countermeasure has a drop greater than 100 pps. - The
ACL.Drop.BL.Pps.On = 100threshold means that the ACL countermeasure will be turned on when the BL countermeasure starts dropping more than 100 pps.
Detect. Added thresholds for the TLS Client Hello rate.
Added thresholds <element>.Input.TLS.ClientHello.{On,Off}, enabling or disabling
countermeasures by the number of TLS ClientHello messages received at the input of
the ATLS countermeasure.
To count TLS ClientHello, the ATLS countermeasure must be enabled or in
autodetect mode.
UX. Added disabling the auto-detection threshold by commenting a line.
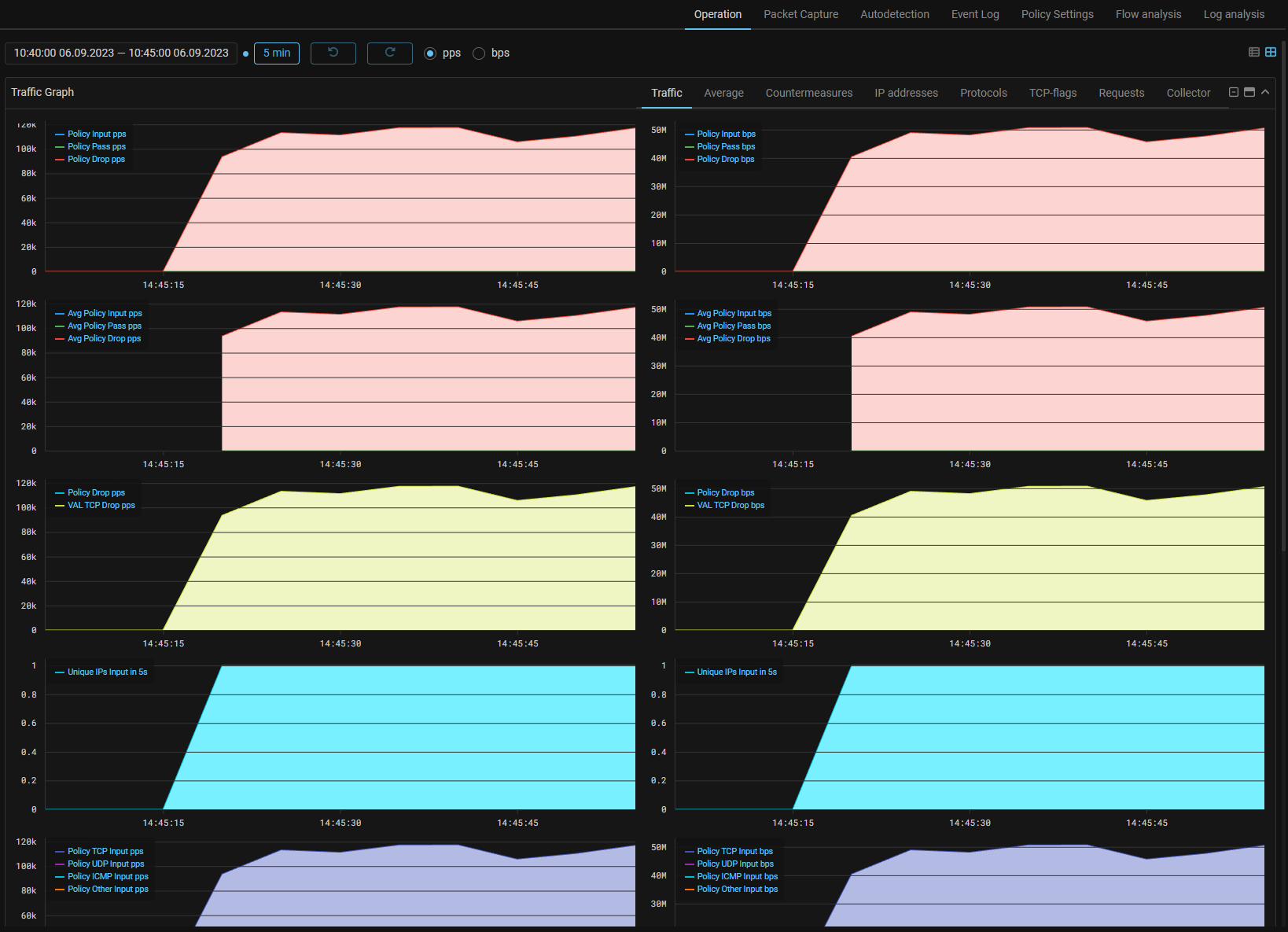
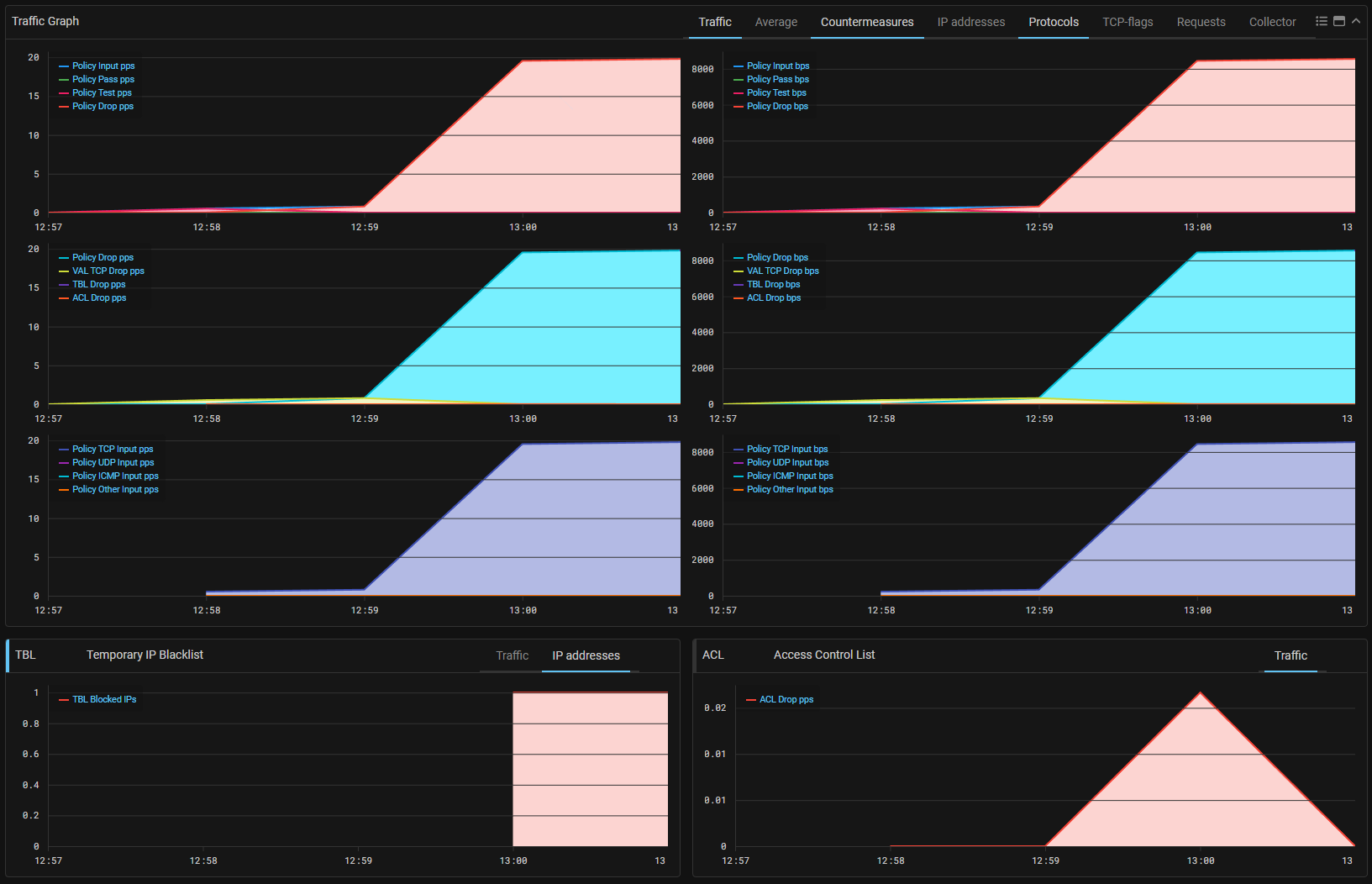
UX. Added a mode of simultaneous display of Traffic Graphs in pps and bps for general protection and policy.
In addition to the simultaneous display, a set of icons to control the display modes of the Traffic Graph has been redesigned.
UX. Added a Traffic Graph tabs display settings.
Now, if the Traffic Graph is expanded, you can turn off the display of unnecessary
tabs.
To do this, click on the name of the tab while holding the Alt key.
Now you can configure the Traffic Graph tabs display.
To enable or disable the display of a tab, you need to click on it while holding down
the Alt key.
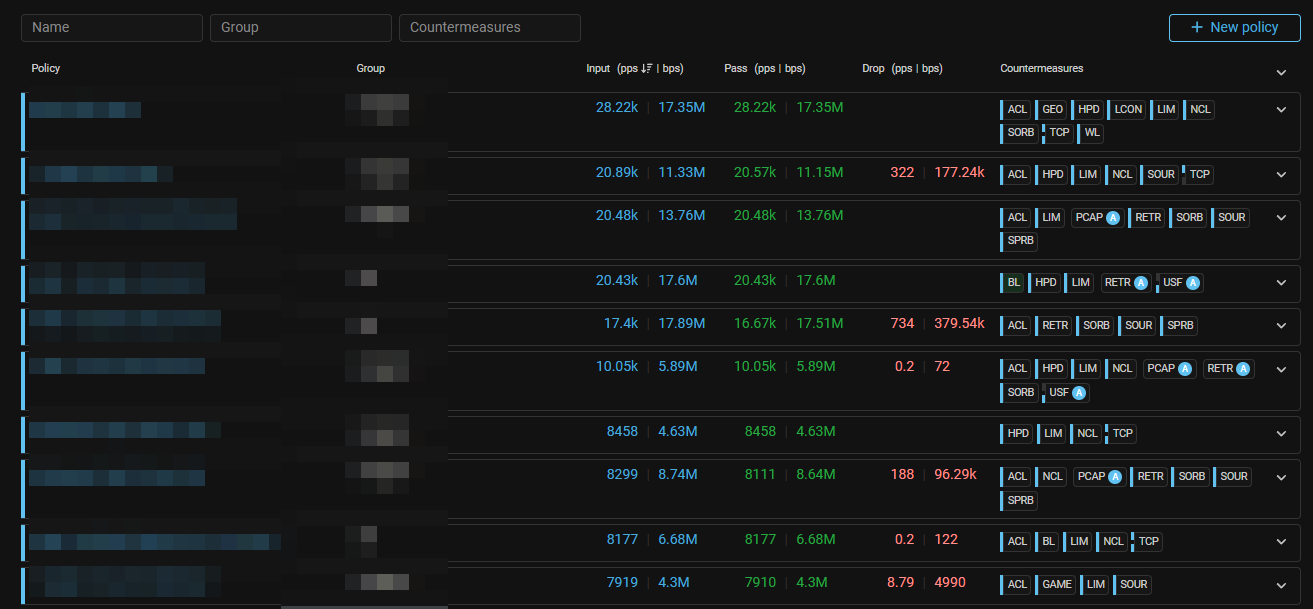
UX. Added sorting for the protection policies list page.
Added the ability to sort protection policies by increasing or decreasing volume of incoming, passed or dropped traffic in pss or bps.