Version v23.06
Version v23.06 adds new HCA and LACL countermeasures, Regular Reports, autodetection
parameters logging. RTS countermeasure has been reworked.
The functionality of Named lists, Log analyzer and TBL, TBL6, ACL, ACL6, TCP,
MINE, ATLS, DTLS, DNS, REX, REX6, ACLI countermeasures has been expanded.
Follow the special instructions to update MITIGATOR to v23.06 version.
Changes in v23.06.8
Core. Added parameter to specify port speed.
port_link_speed parameter to specify port speed has been added to
data-plane.conf file.
Specifying this parameter disables autonegotiation and ports rise at
the specified speed if they can.
The speed of a particular port can be specified with the link_speed
parameter in the section for that port.
Changes in v23.06.2
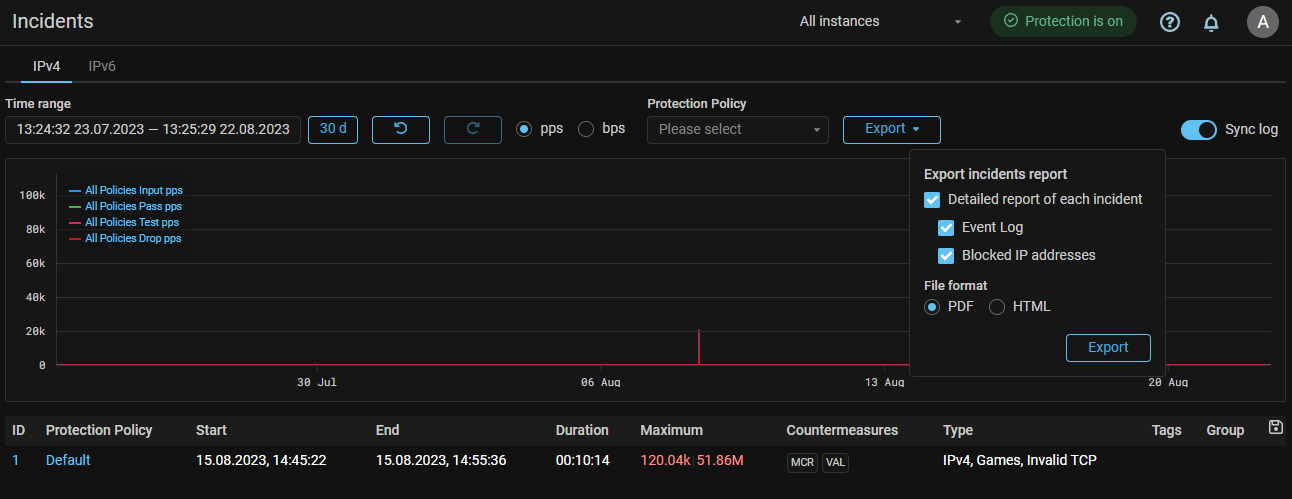
Reports. Information on graphs and routing rules has been added to the incidents report.
Traffic graphs and routing rules to the policy at the start of the incident has been added to the exported incident reports.
Reports. An extended report on a specific incident has been added.
You can now add extended information on individual incidents to the Incident Report.
Changes in v23.06
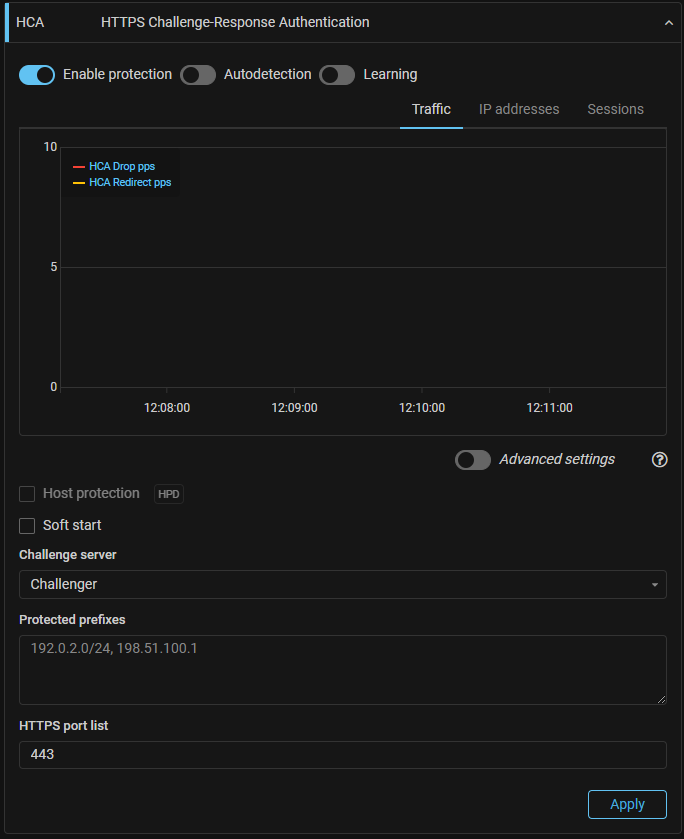
HCA. New countermeasure has been added to protect HTTPS with decryption.
HCA authenticates IP addresses using the challenge-response method inside HTTPS.
For the countermeasure to work, you must set TLS certificates and secret keys for protected domains in the system settings.
The mechanism is in experimental mode. Feature is licensed separately.
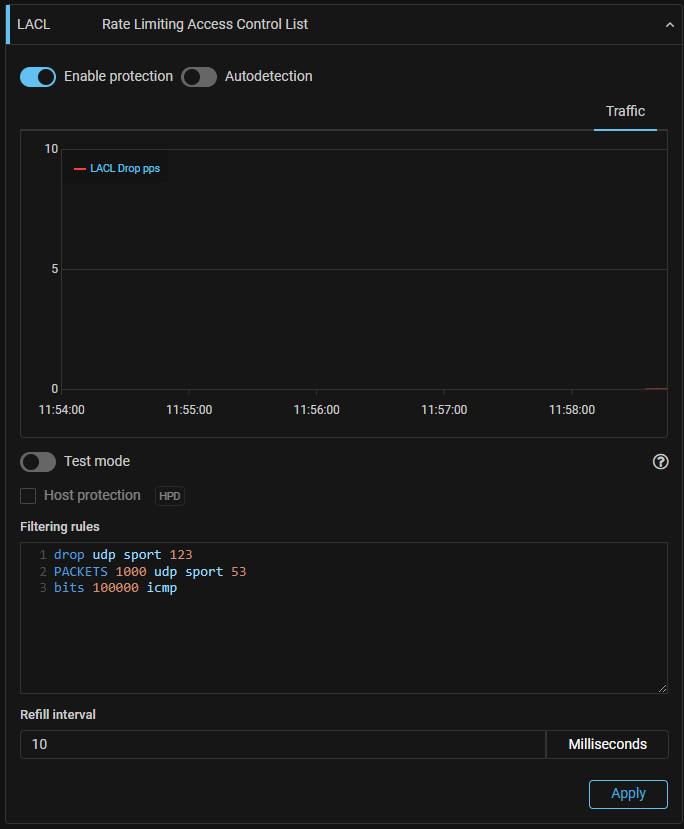
LACL. A new countermeasure that restricts traffic by rules has been added.
LACL countermeasure has been added to IPv4 and IPv6 General protection. In terms of syntax, the countermeasure is similar to ACL, and has the same set of filtering components for L3 and L4 headers, but a different set of actions on traffic.
The countermeasure provides following actions:
PASS– pass;DROP– drop;PACKETS<number>– limit in pps;BITS<number>– limit in bps;PACKETS<number>BITS<number>– limit in pps and bps.
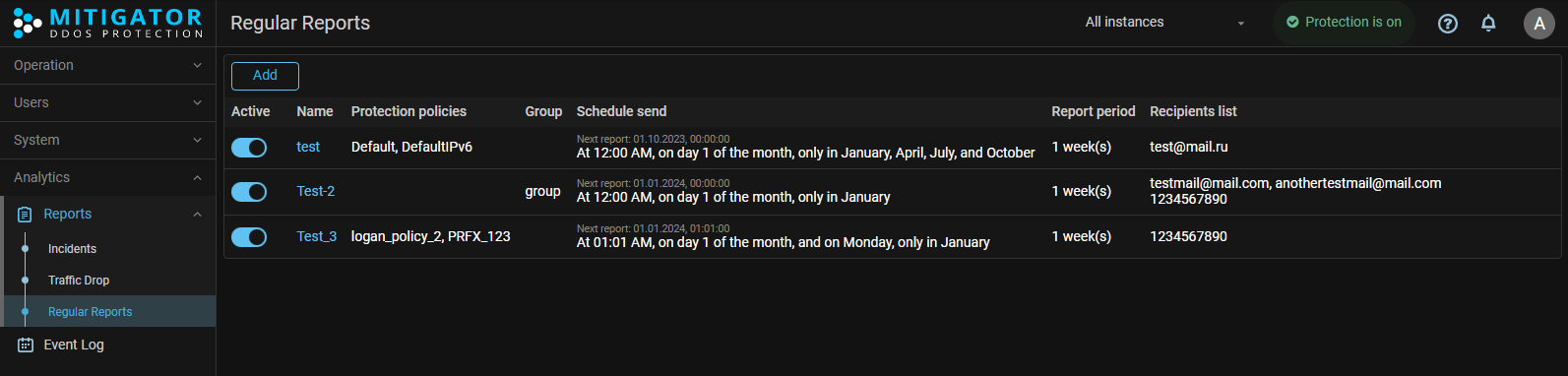
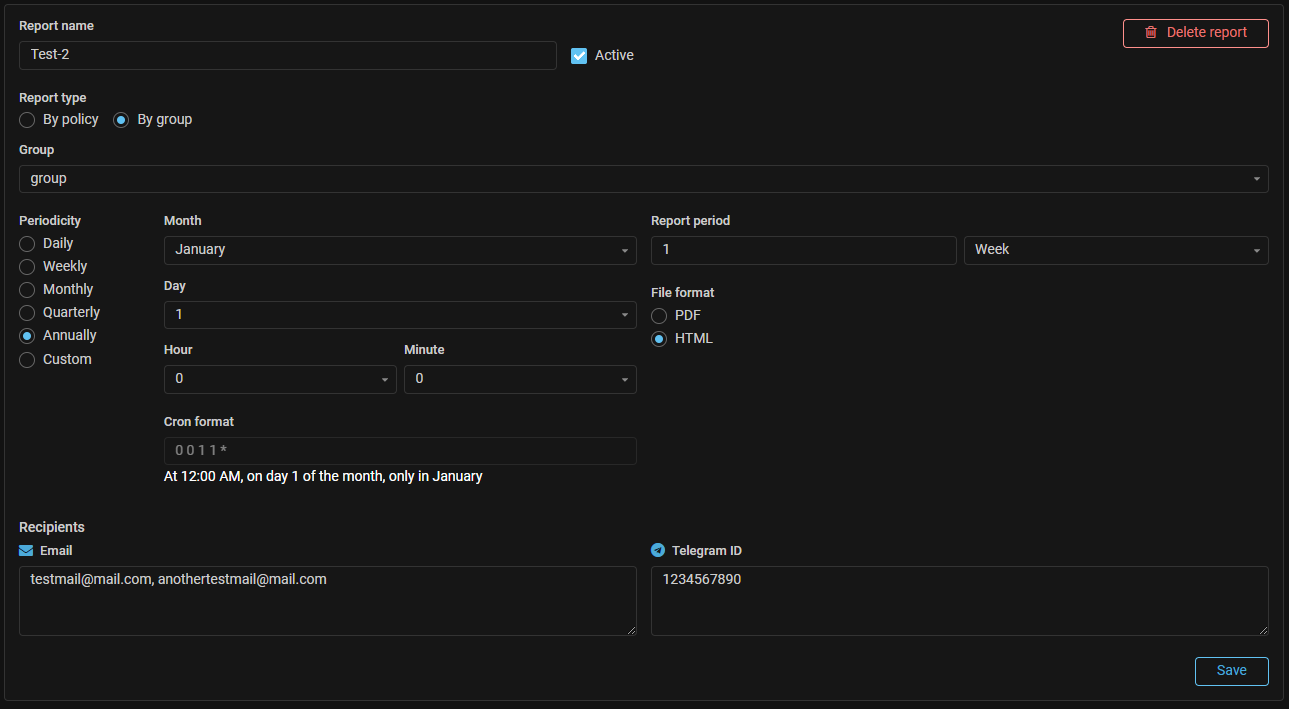
Reports. A mechanism for generating and regularly sending reports has been added.
A new “Regular reports” page has been added to “Reports” section of the Web interface. Tasks for sending regular reports are created on the page. At the moment, the reports contain information about incidents. Information on other entities is planned to be added in the future.
When creating a task, you need to specify on which policy or group incidents should the regular report be generated. The sending periodicity and the time period for which data will be included in the report are configured.
The sending periodicity can be selected from predefined options, or you can set your own periodicity parameters in the Cron format. If necessary, you can send the report to the recipients immediately.
The report can be sent by email or via Telegram. Mail server settings and Telegram token must be set at “Settings” page. The report format is HTML or PDF.
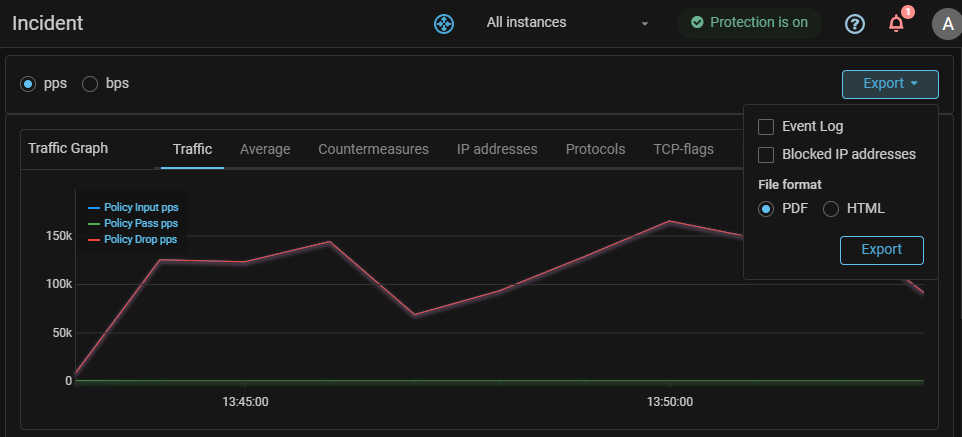
Reports. Incident report export has been added.
Report export in PDF and HTML formats has been added to the “Incident” page.
RTS. The signature generation mechanism has been redesigned.
To reduce false positives when applying filtering rules generated by a countermeasure, signature generation algorithms have been redesigned and improved. The countermeasure analyzes L3 and L4 headers, the ability to generate L4 payload is temporarily disabled. The mechanism requires the use of reference traffic. The dump with reference traffic must be loaded into the countermeasure, and the “Use reference traffic” checkbox must be set in the countermeasure parameters.
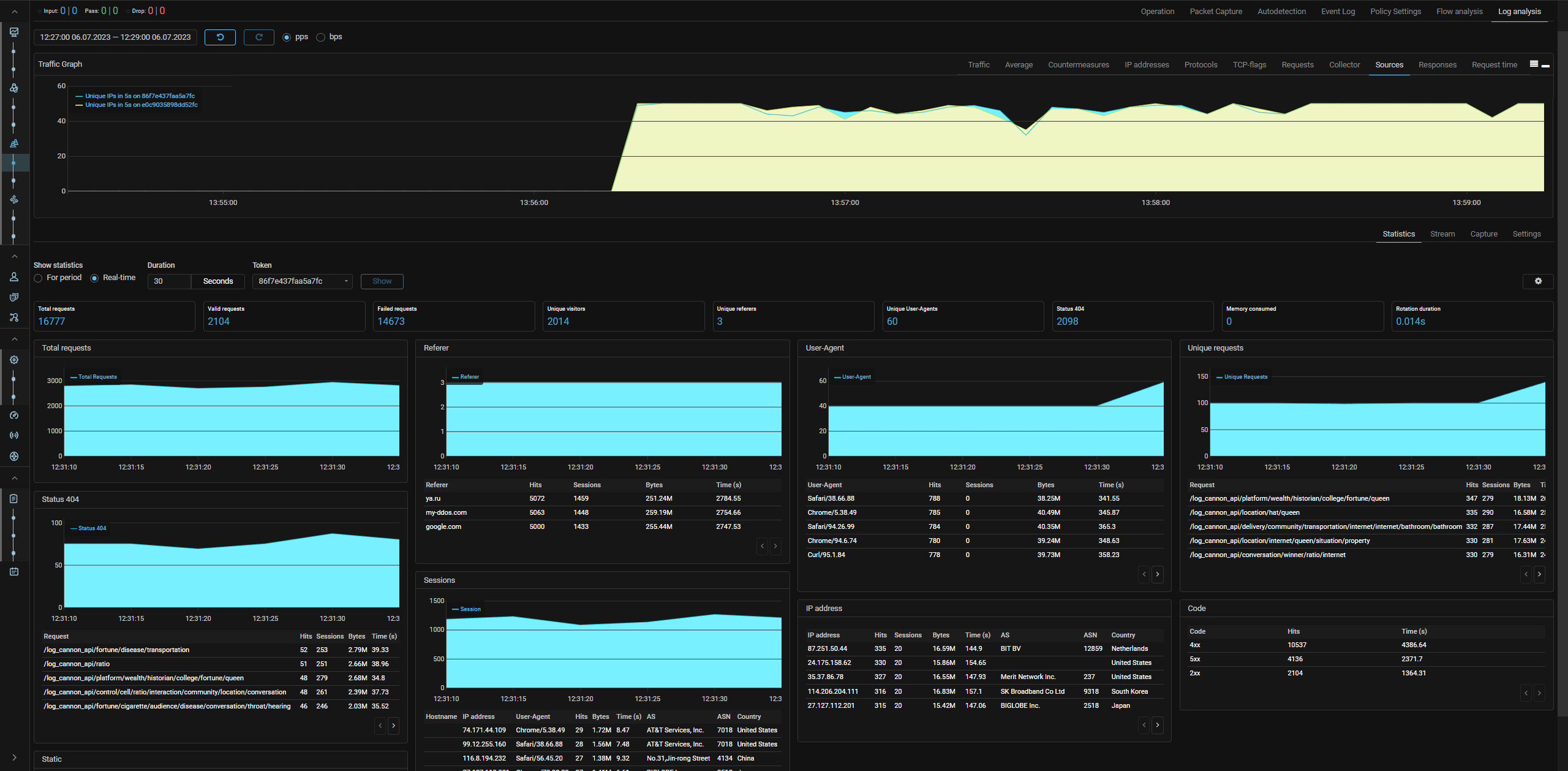
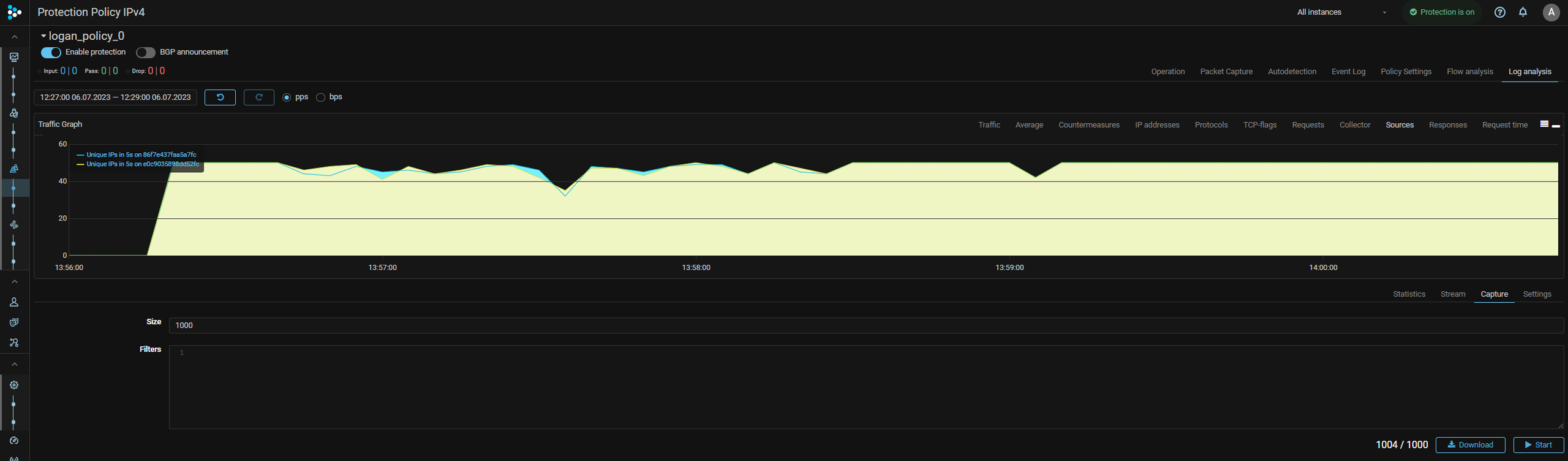
LOGAN. Statistics on received logs has been added.
“Statistics” tab has been added to LOGAN. The tab displays statistics on logs received from the protected Web server in various sections. Statistics is built on the selected unique Web server token. You can view statistics for a fixed period or in real time. Flexible settings for displaying statistics by the number of charts and tables on the screen, by the number of records in the top are available.
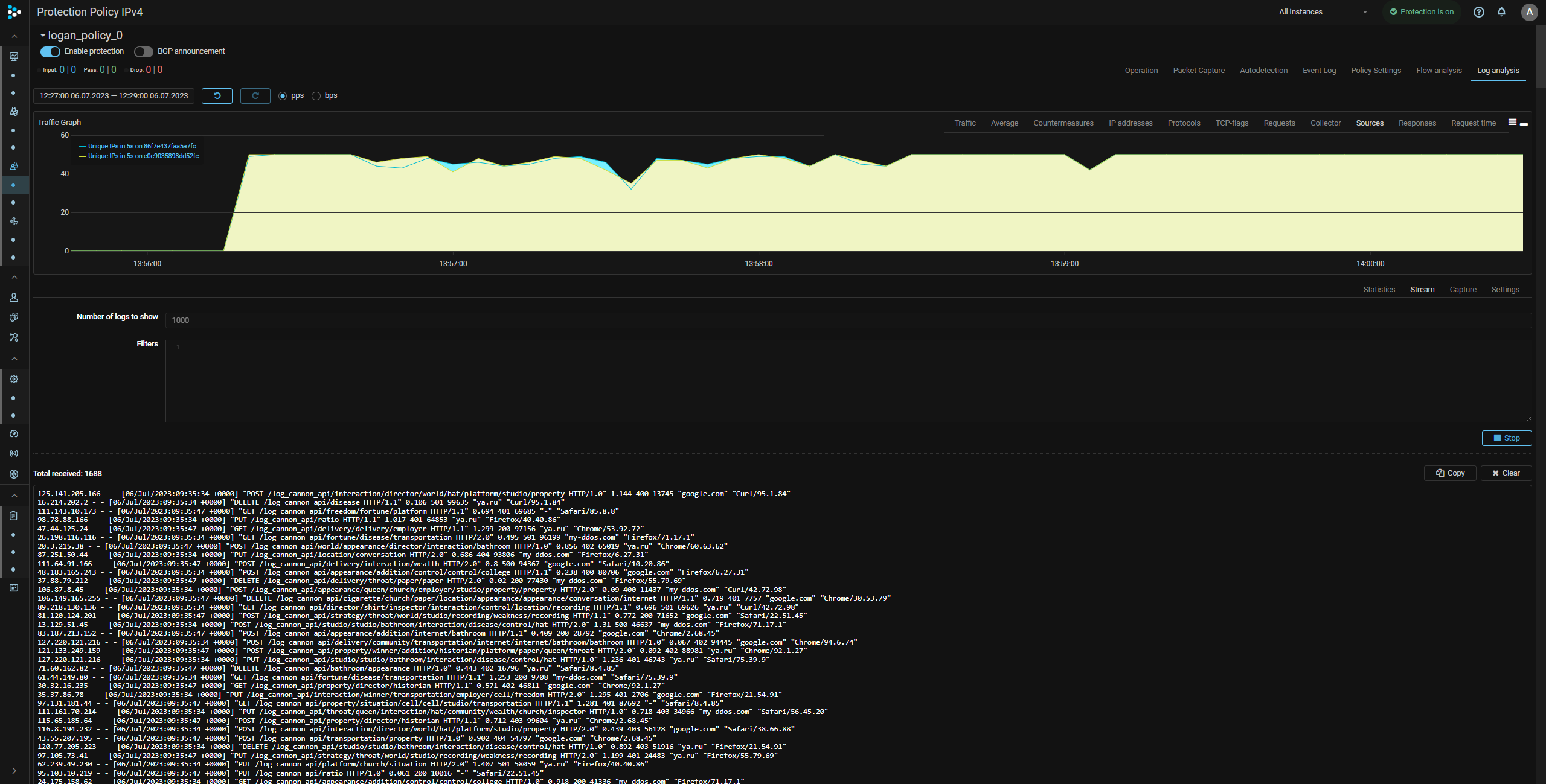
LOGAN. Real-time log view has been added.
“Stream” tab has been added to LOGAN. The tab displays real-time logs received from the Web server. The number of records displayed is configurable. If necessary, the output can be filtered using filters by:
- unique Web server token;
- Source IP address;
- request body;
- User-Agent;
- Referer;
- status code;
- request processing time.
Filters can be combined with each other. One filtering rule is one line. There is a logical “AND” between the filters in one rule. There is a logical “OR” between the rules.
Example:
src 1.2.3.0/24 user-agent bot
status (401, 403) request admin.htmlLOGAN. Logs capture has been added.
“Capture” tab has been added to LOGAN. On the tab, you can start capturing web server logs to a capture file. The number of records that will be included in the capture file is configured. Filtering is available using the same filters as on the “Stream” tab.
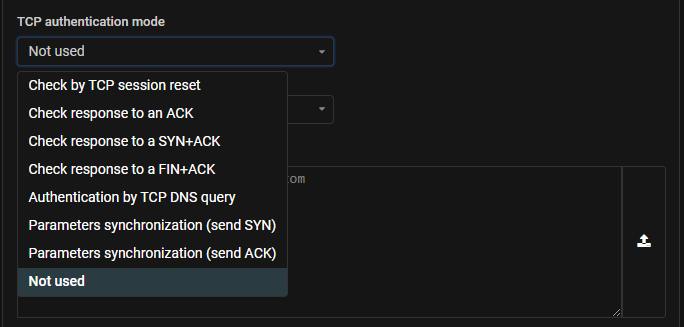
DNS. TCP authentication mode with ISN parameters synchronization has been added.
Now TCP authentication can be performed without session reset by synchronizing the ISN parameters with the protected DNS server in two ways, depending on the presence of a stateful firewall in front of the protected server.
TCP. ISN parameters synchronization mode with stateful firewall in front of the protected server is now supported.
ATLS. ISN parameters synchronization mode with stateful firewall in front of the protected server is now supported.
MINE. ISN parameters synchronization mode with stateful firewall in front of the protected server is now supported.
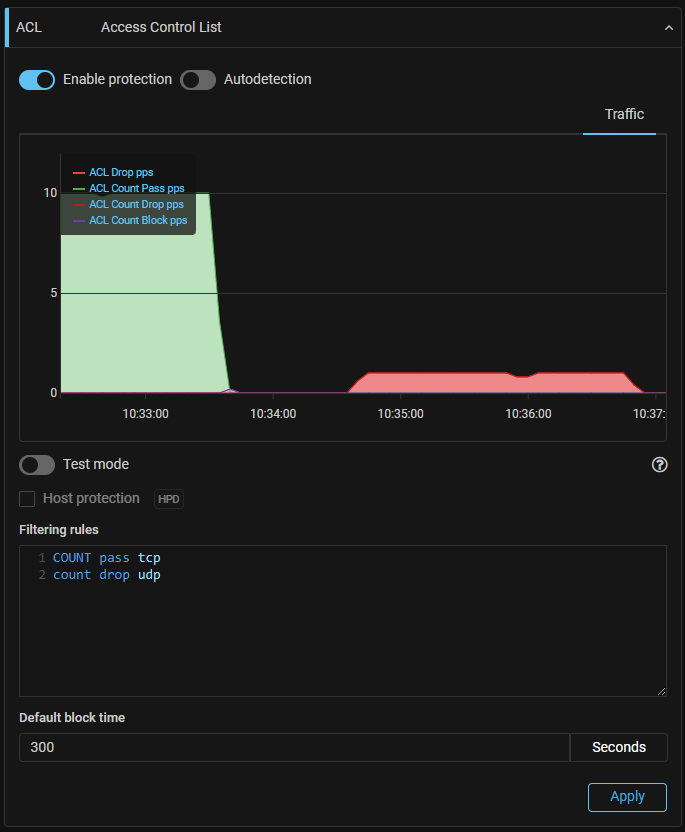
ACL. COUNT action has been changed.
Previously, COUNT was a separate action by which a packet matching a rule passed to countermeasure output and was counted. Now COUNT is a flag that can be set for any action. If the flag is set, the packet is counted and displayed on the graph corresponding to the action.
Thus, the countermeasure provides for the following actions:
PASS– pass;DROP– drop;BLOCK– block;COUNT PASS– count and pass;COUNT DROP– count and drop;COUNT BLOCK– count and block.
ACL6. COUNT action has been changed.
ACLI. COUNT action has been changed.
The changes are similar to those in the ACL countermeasure.
REX. COUNT action has been changed.
The changes are similar to those in the ACL countermeasure.
REX6. COUNT action has been changed.
The changes are similar to those in the ACL countermeasure.
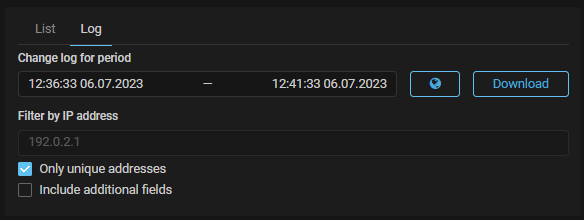
TBL. Only unique IP addresses download option from the block log has been added.
TBL6. Only unique IP addresses download option from the block log has been added.
DTLS. Added support for DTLS version 0x0100.
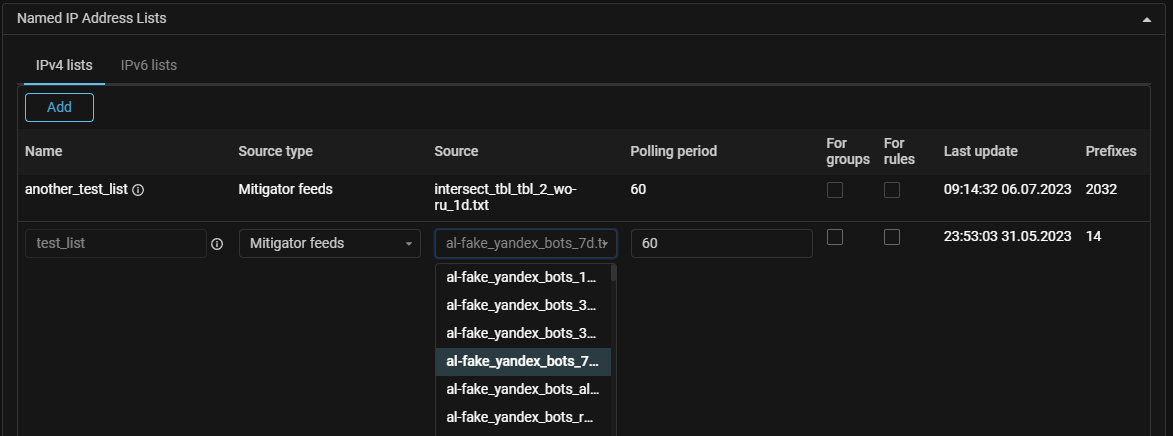
IPList. A new type of source "Mitigator feeds" has been added.
You can now specify “Mitigator feeds” as the source type when creating a named list of IP addresses. The feed selected from the drop-down list will be installed into the system from the analytics server. Name filtering is available. The list update period is similar to the “HTTP” source type.
An access token to the analytics server is required in the system settings. To obtain a token, contact your account manager.
IPList. Support fot autonomous system numbers has been added.
The autonomous system numbers in the Named IP Address Lists can now be specified in the
form as123456.
JA3Lists. A new type of source "Mitigator feeds" has been added.
Signatures. The signature databases from the MITIGATOR team have been moved to the analytics server.
Now, to download and install the signature database in the “REX-signatures Management” panel of the “Settings” page, you need to specify an access token to the analytics server in the “Analytics Server” panel.
EventLog. Autodetection threshold changes are logged now.
Now, when the autodetection thresholds are changed, the changed values are displayed in the “Details” field of the event log.
Collector. Reports downloading has been added to Flow Analysis page.
Now on the “Flow Analysis” page you can download CSV files with data for the specified time interval, similar to the “Flow Analysis” tab of the “Protection Policy” page.
Core. Updated DPDK to v23.03.
Core. Metrics storage has been optimized.
Metrics now take up less disk space.
pgfailover. Added the parameter for the number of connections to the database.
The number of connection attempts is controlled by the -attempts parameter. 1 by default.
pgfailover documentation.
UX. Backend response display for user action in Web interface has been added.
The mechanism allows to get response without the neccesity to view logs or use browser developer tools.