Identifying patterns with a decision tree
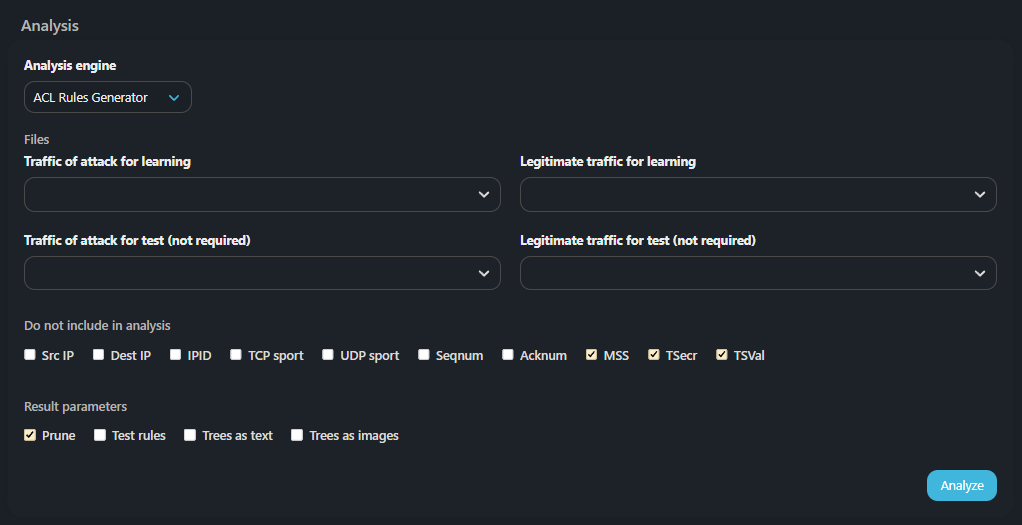
The mechanism analyzes dumps of legitimate traffic and attack traffic and generates a set of ACL filtering rules. IP, TCP, UDP and ICMP protocol packets are analyzed.
Traffic dumps are selected from the drop-down list, for which they must be previously uploaded to the service on the Uploads tab. Optionally, you can specify additional dumps on which the rules obtained during the analysis will be tested. If no additional dumps are specified, then the training dumps are divided proportionally into a training part and a test part.
The following can be excluded from the analysis and ignored in the generated rules:
- Src IP — source IP address;
- Dst IP — destination IP address;
- IPID — IP protocol ID;
- TCP sport — TCP sender port;
- UDP sport — UDP sender port;
- Seqnum — TCP Sequence number;
- Acknum — TCP Acknowledgment Number;
- MSS — maximum size of TCP segment;
- TSecr — TCP Timestamps Option TS Echo Reply;
- TSVal — TCP Timestamps Option TS Value.
The following checkboxes can be activated to analyze patterns using the decision tree:
- Prune — add generalized trees and rules to the report instead of specific ones;
- Test rules — add information about the results of testing of the generated rules on the loaded dumps to the report;
- Trees in text — add decision trees to the report in text form;
- Trees in pictures — create an archive with a graphical representation of decision trees.
Report
The report consists of fundamentally identical sections written for each of the IP, TCP, UDP and ICMP protocols, provided that the packets of the corresponding protocols are found in the dump. Each section contains the following:
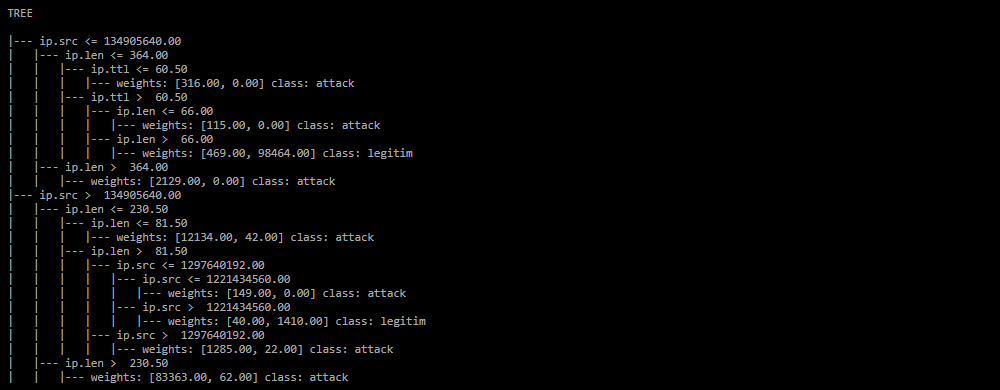
Decision tree in text form. The section is formed in the report if the checkbox Trees in text is set.
-
Reset indicators when applying the rules generated by the analysis on legitimate and attack traffic, obtained during testing in absolute and relative values.
-
Filtering rules generated by the mechanism during the analysis of traffic dumps.
-
Duration:
Processing duration.