Version v22.12
Version v22.12 adds new DTLS and JA3 countermeasures, external sources of named ACLs,
new auto-detection thresholds based on collector data.
The functionality of named lists, BGP and WL, WL6, RETR, RETR6, DNS, ATLS
countermeasures has been expanded. FRB countermeasure had been added to the general
protection.
Before updating MITIGATOR, you need to make sure that the
Docker
version is up to date on all of the system instances
(for docker-ce — 20.10.10+, for docker.io — 20.10.5+). It is recommended
to update from the software repositories for your OS.
Changes in v22.12
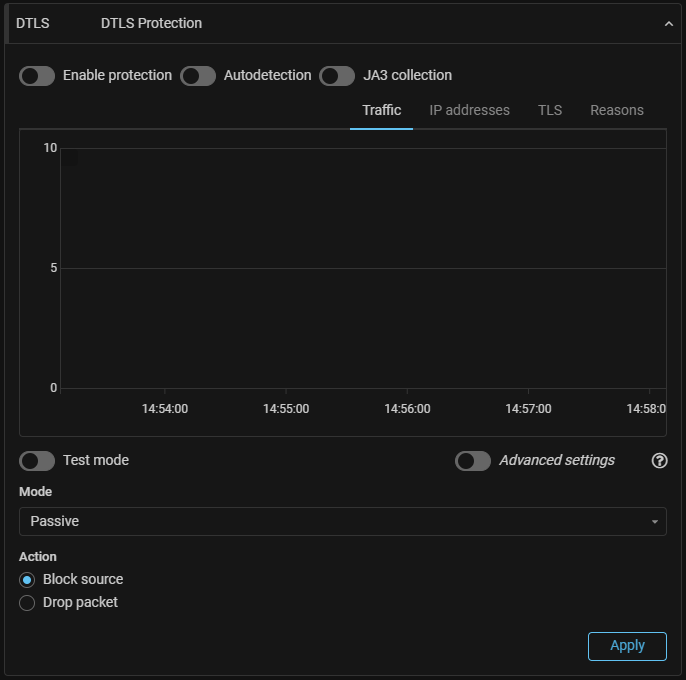
DTLS. The “DTLS Protection” countermeasure has been added to the IPv4 protection policy.
The countermeasure can work in multiple modes: one passive and five active. DTLS 1.3 is supported. The filtration by JA3 fingerprints, TLS Cipher Suite and TLS Extension is identical to ATLS countermeasure.
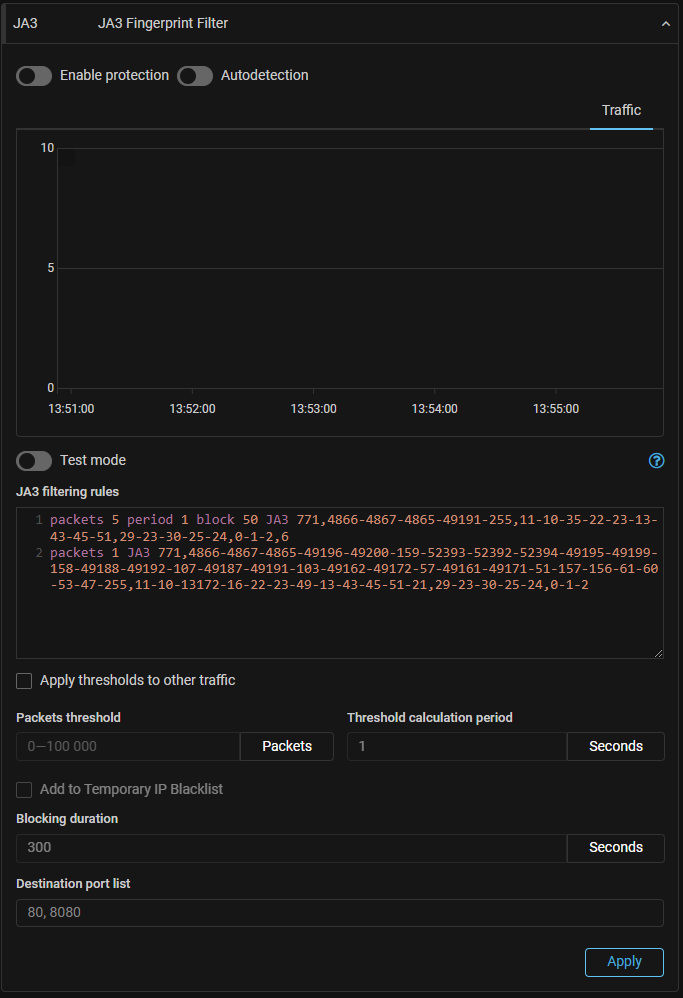
JA3. The “JA3 Fingerprint Filter” countermeasure has been added to IPv4 protection policy.
The countermeasure blocks the passage of the packets from the IP address, containing “ClientHello” TLS message with specific JA3 fingerprints, if their number exceeds the threshold for the given time period. Blocking occurs when the countermeasure engine detects that the threshold has been exceeded and is retained until the number of packets with JA3 fingerprint data falls below the threshold.
The countermeasure can also block the passage of network packets whose content does not match any of the specified rules. This function can be used simultaneously or independently with rules. If no rules are set, then the countermeasure blocks traffic from the IP address, similar to the SORB countermeasure.
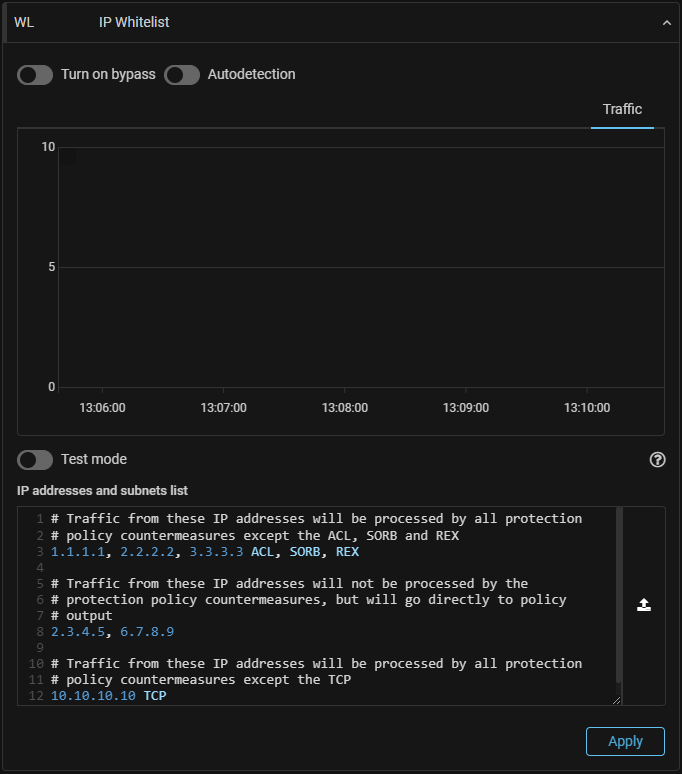
WL. The ability to pass a packet without the procession by specific countermeasures only has been added.
Now, in the “IP Whitelist” countermeasure in protection policies, next to the prefix value, you can specify a list of countermeasures that should not process traffic of this prefix.
Prefixing uses the bypass list that is higher in the list, so more specific prefixes should appear above less specific ones in the list.
WL6. The ability to pass a packet without the procession by specific countermeasures of the protection policy only has been added.
ATLS. Mechanism for checking L4-payload by regular expressions has been added.
Now the user can specify regular expressions for L4-payload in the countermeasure. This mechanism can be used, for example, to block senders of HTTP requests to port 443, by specifying the characteristic substrings.
ATLS. The ability to skip segmented TLS ClientHellos without processing has been added.
Packets containing segmented ClientHello messages can now be passed without processing. Such packages will also be ignored by the JA3 fingerprint collection mechanisms.
FRB. “Flow Rate Blocking” countermeasure has been added to IPv4 general protection.
RETR. The mode skipping TCP segments without payload has been added.
To authenticate an application by the first request in TCP,
it is necessary to ensure the smooth passage of packets to establish a connection.
The pass-handshake keyword can now be specified in the rule, allowing the packets
needed to establish a connection to be passed through without being processed.
RETR6. The mode skipping TCP segments without payload has been added.
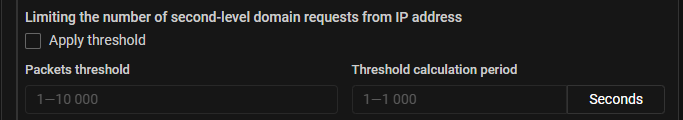
DNS. DNS limiter for requests from a second-level domain from one IP address has been added.
The mechanism limits the number of DNS requests with one second-level domain
name from one IP address in a given period. For example, if a limit of
10 requests is set, and the IP address sent 5 requests
with the domain name example.com, 3 requests with the domain name
x.example.com, and 2 requests with the domain name y.example.com,
then restriction will work.
When the countermeasure mechanism detects that the threshold has been exceeded, all DNS requests for the given domain name from this IP address are dropped. DNS requests with other second-level domain names continue to go through.
DNS. Support for Cyrillic characters in domain names lists has been added.
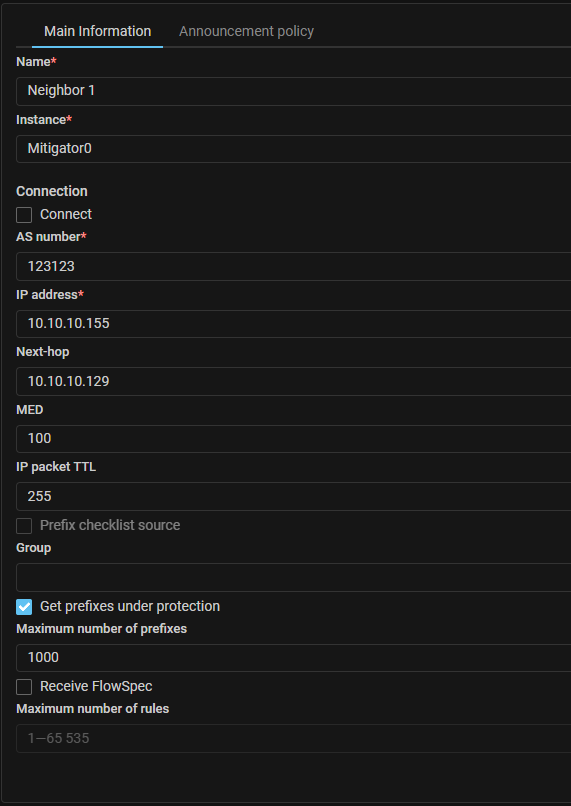
BGP. The ability to send prefix traffic received from a BGP neighbor for cleaning has been added.
New system lists system.protected.prefixes and system.protected.prefixes.checked
have been added, allowing to fully implement the signaling scenario between client
and operator MITIGATORs without using additional route reflectors. The lists are filled
with the values of prefixes received from the BGP neighbor, whose settings have the
“Get prefixes under protection” flag set. If a group is specified, then prefixes
are checked to see if they belong to a group. It also specifies the maximum number
of prefixes that a given BGP neighbor can report.
A BGP neighbor cannot be both a source of prefixes directing the scrubbing and a source of test prefixes.
BGP. MED attribute to BGP neighbor settings has been added.
An attribute defining the priority of the traffic route from the BGP neighbor to the MITIGATOR instance has been added. If there are multiple peer routes to an instance, the route with the lowest MED value will be chosen.
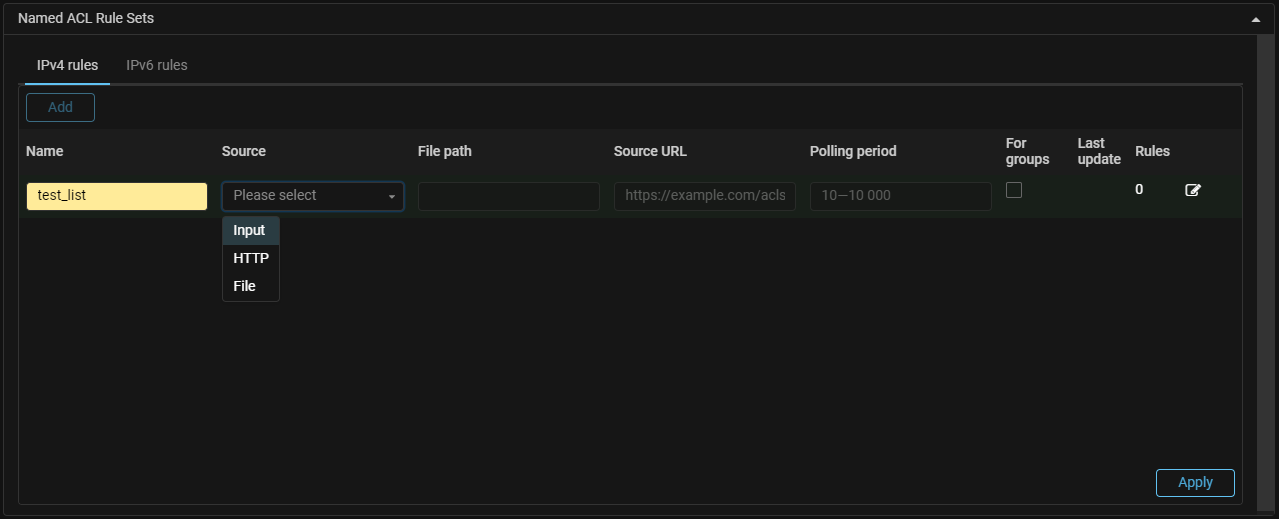
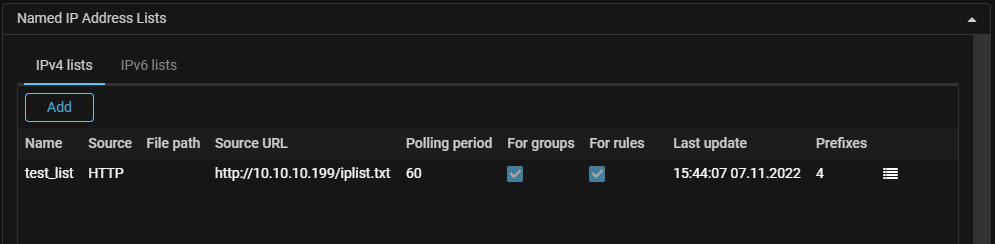
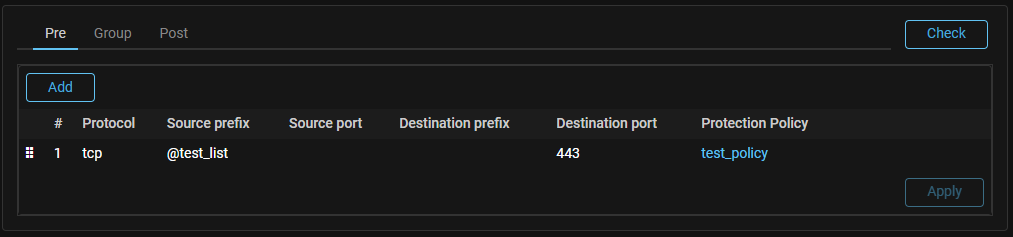
NamedACL. Sources for loading of the named sets of filtering rules have been added.
Now named lists of filtering rules containing named sets of filtering rules, like named lists of IP addresses, can be loaded from an external HTTP or HTTPS resource, from a file mounted in the backend container, or entered manually.
IPList. Added support for named lists of IP addresses in routing rules.
Named lists of IP addresses can now be used in protection policies routing rules to specify sender or recipient prefixes. When you specify a named list in a group policy routing rule, a check is made to see if the values in the list match the group prefixes. If the list contains prefixes that are invalid for the group, the rule cannot be saved. If an invalid prefix was added to the list after it was applied in a routing rule, that prefix will not be considered by the rule.
If a named list is allowed to be used in protection policies routing rules, it cannot be used in countermeasures.
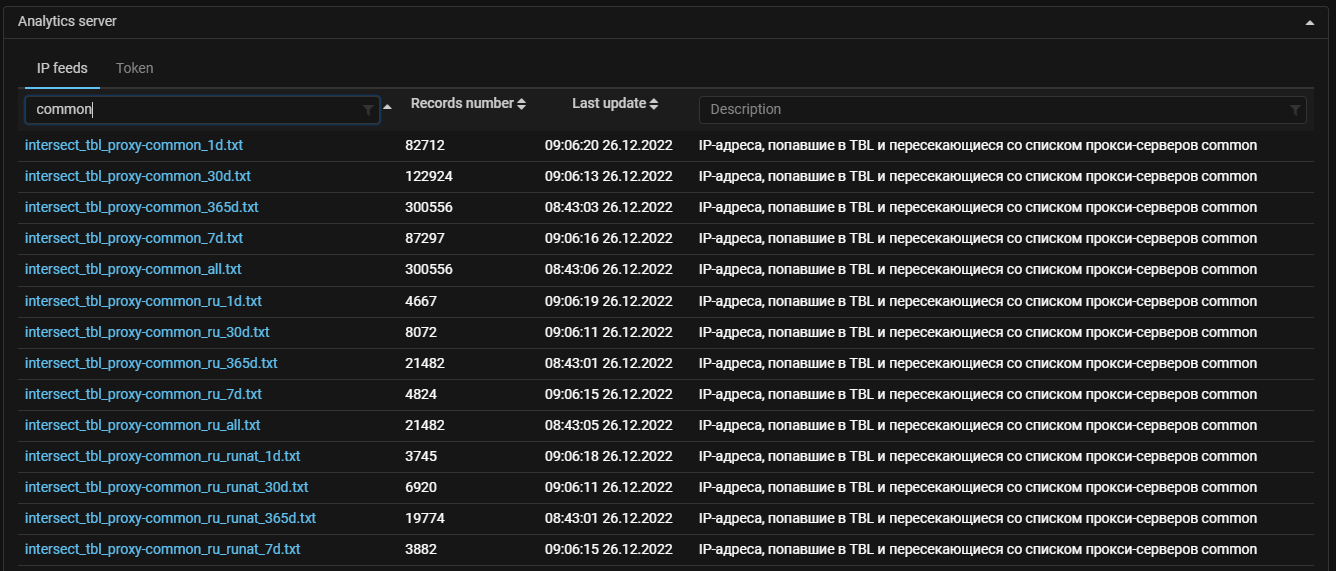
Analytics server. A list of all feeds available by token from the analytics server has been added to the system settings.
Analytics server panel has been reworked. Now if you specify a server access token, the “IP feeds” tab appears with a list of all available feeds. For each feed, the list displays the number of entries, the date and time it was last updated, and a description. The feed can be downloaded by clicking on the title.
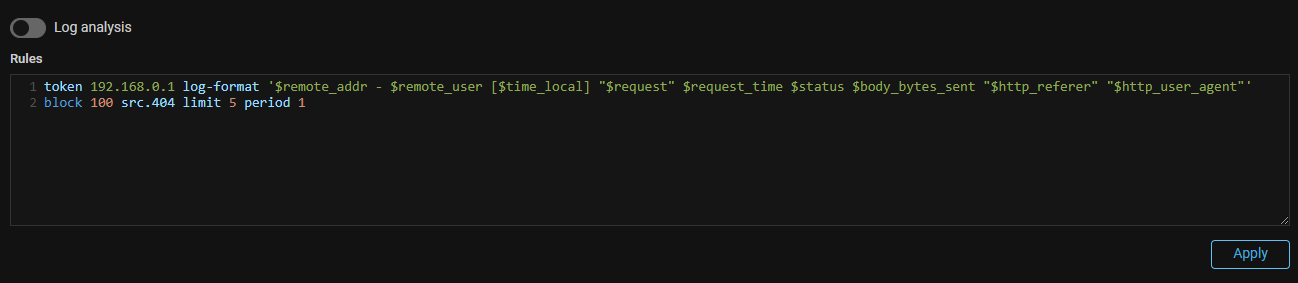
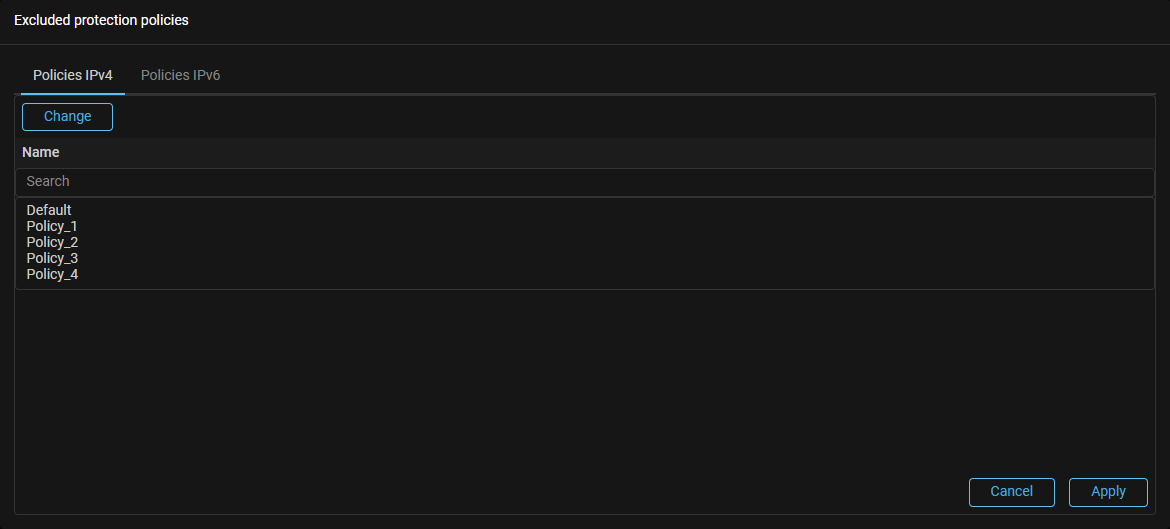
LogAnalyzer. Deactivation of the log analyzer has been added in the protection policy.
Now you can disable the log analyzer in the protection policy, while all other policy mechanisms will continue to work.
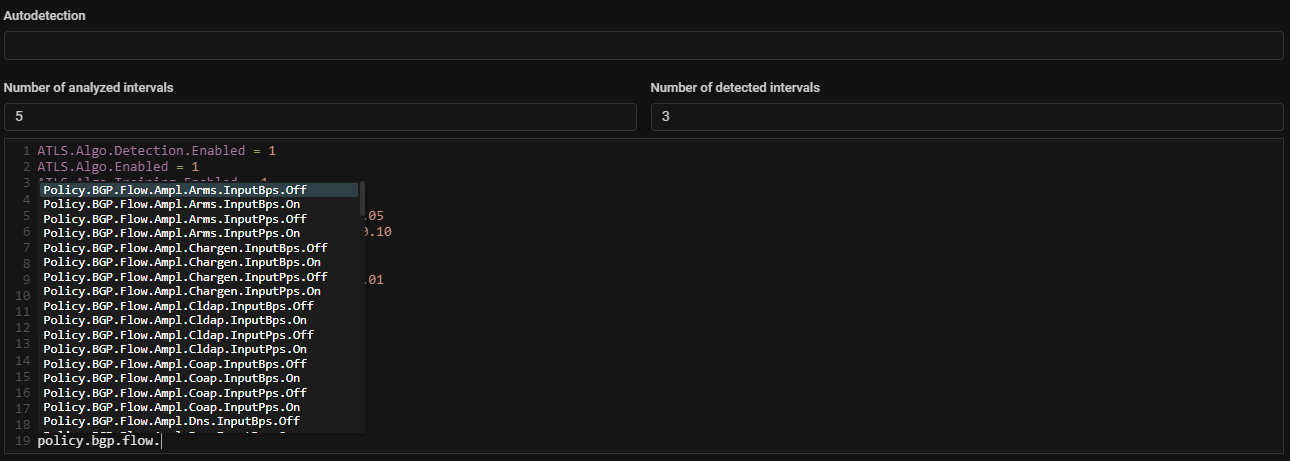
Detect. News thresholds for BGP announcement activation based on data from the collector have been added.
Now BGP announcement can be activated not only by the total volume of traffic on the collector, but also by exceeding the threshold of a specific type of traffic.
Policy.BGP.Flow.Ampl.*— UDP traffic thresholds from different ports (different types of UDP amplifications);Policy.BGP.Flow.Dns.*— DNS traffic;Policy.BGP.Flow.Icmp.*— ICMP traffic thresholds;Policy.BGP.Flow.IpFragment.*— fragmented traffic thresholds;Policy.BGP.Flow.IpPrivate.*— thresholds for traffic from IPs from the range of internal addresses;Policy.BGP.Flow.IpProtocol0.*— IPv4 traffic thresholds;Policy.BGP.Flow.NetBios.*— UDP traffic thresholds from 137 port;Policy.BGP.Flow.RipV1.*— UDP traffic thresholds from 520 port;Policy.BGP.Flow.RpcBind.*— UDP traffic thresholds from 111 port;Policy.BGP.Flow.Tcp.*— TCP traffic thresholds;Policy.BGP.Flow.TcpNull.*— TCP traffic thresholds without TCP flags;Policy.BGP.Flow.TcpRst.*— TCP traffic thresholds with RST flag;Policy.BGP.Flow.TcpSyn.*— TCP traffic thresholds with SYN flags;Policy.BGP.Flow.Udp.*— UDP traffic thresholds;Policy.BGP.Flow.mDns.*— UDP traffic thresholds from 5353 port.
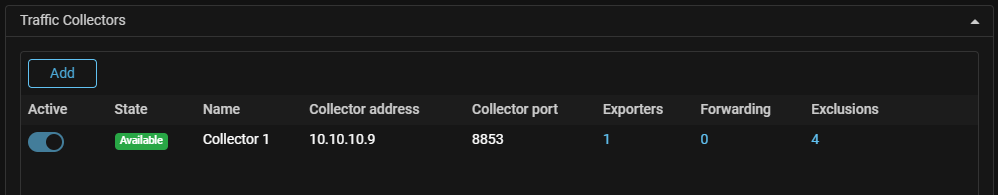
Collector. The ability to cease the storage of the flow for selected policies has been added.
Now, when configuring a collector, you can list the protection policies whose flow will not be taken into account by the collector.
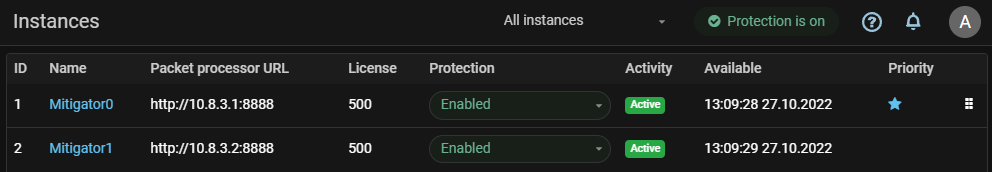
UX. Display of the availability time of all cluster instances has been added.
The “Available” field now displays the last poll time of all cluster instances, not just the ones participating in leader election.
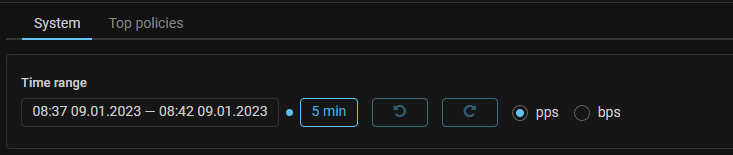
UX. Buttons for switching periods on the “Dashboard” page had been added.
Now “System” and “Top policies” tabs of the “Dashboard” page have buttons to
switch between previously used time periods back and forth. Also, to switch
periods, you can use the keyboard shortcuts ALT + Z - for the previous period
and ALT + C - for the next period.
UX. Now the calendar and the list of predefined intervals are summoned not only by clicking on the time range filter field, but also by clicking on the icon of the current interval.