TLS Analyzer
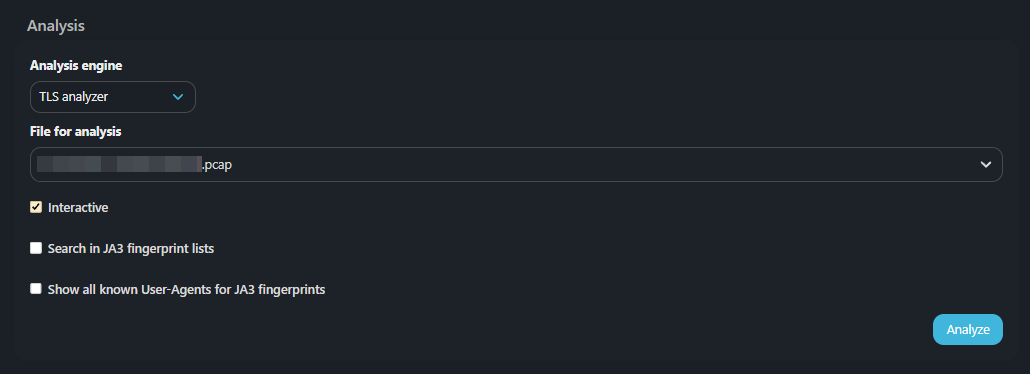
This method accepts PCAP or a text file as input. JA3 fingerprints are extracted from PCAP and additional information is displayed. Text files analysis allows you to match JA3 hash, JA3 fullstring or User-Agent. For example, you can get JA3 hash and User-Agent list by uploading JA3 fullstring. And if the User-Agent value is entered, then the search will be performed for records that have such a substring in the User-Agent.
The sections inside the report are presented in CSV format so it can be easily analyzed in other tools like Excel or Jupyter.
The following checkboxes can be activated for this mechanism:
- Interactive — an interactive HTML report is formed instead of a text one;
- Search in JA3 fingerprint lists — add a section to the report displays the results of JA3 fingerprints checking against reputation lists;
- Show all known User-Agents for JA3 fingerprints — add a section to the report displays all observable User-Agents for each JA3 fingerprint in the file.
Report
The report can be generated as a text file or as an interactive HTML page if the Interactive checkbox is set. The content of the report does not depend on the presentation form, but the interactive version has some advantages and is more convenient to use, so the report description is based on it.
The interactive report can be exported to an HTML page or JSON for later use outside of the PSG.
Each section can be collapsed. Inside the sections responsible for checking against reputation lists, a list of all sources that included the analyzed JA3 fingerprints is provided. Filtering by values and tables export to CSV are provided.
If a text file is fed to the input, the general appearance of the report does not change, but not all of its sections will be filled. The “User-Agent by JA3” and “User-Agent Analysis” sections are always filled. “Approved fingerprints” is filled if the file contained fingerprints in JA3 fullstring format.
The report contain sections:
-
- JA3 — recognized JA3 fingerprints;
- Unique JA3 — number of unique JA3 fingerprints in the dump;
- JA3 fullstring — number of fingerprints in JA3 fullstring format;
- Unique JA3 fullstring — number of unique fingerprints in JA3 fullstring format;
- Approved Fingerprints — number of unique valid fingerprints;
- Rejected Fingerprints — number of unique invalid fingerprints;
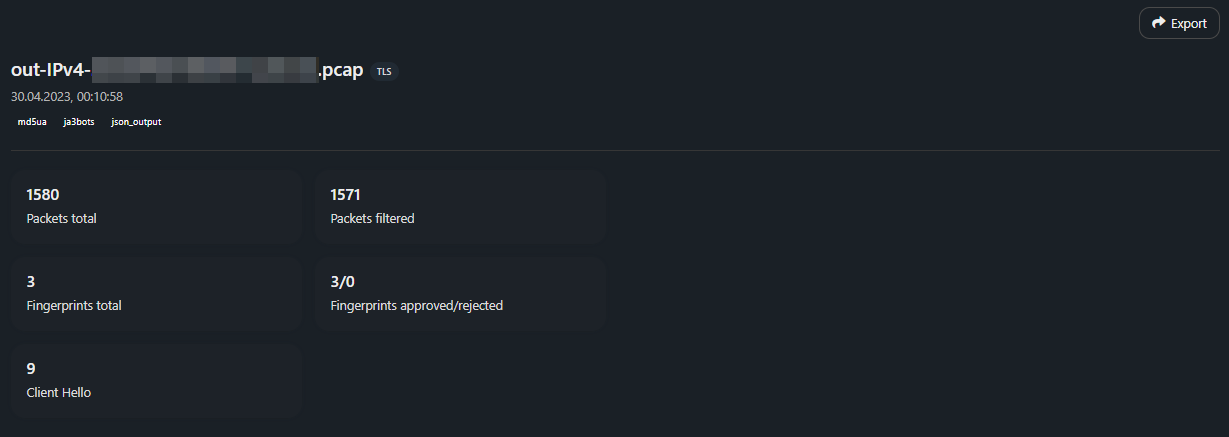
- Packets total — number of packets in dump;
- Packets filtered — number of packets analyzed;
- Client Hello — number of ClientHello;
- IPs total — number of unique source IP addresses in dump.
-
Approved fingerprints;
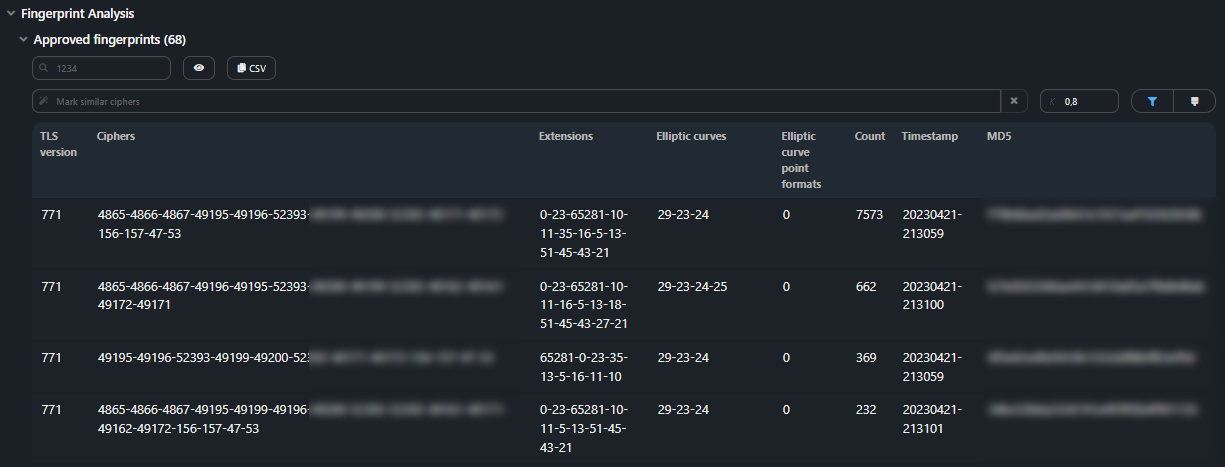
 Tables of unique valid and invalid JA3 fingerprints observed in the dump in descending
order of quantity.
For more convenient comparing JA3 fingerprints with each other provided:
Tables of unique valid and invalid JA3 fingerprints observed in the dump in descending
order of quantity.
For more convenient comparing JA3 fingerprints with each other provided:- Fields display turning off;
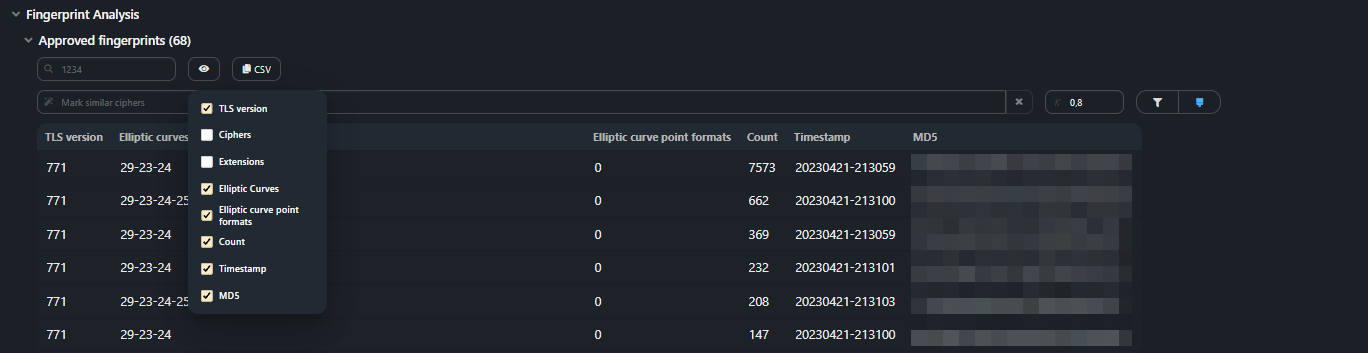

- Similar fingerprints highlighting.
Fingerprints are compared by Ciphers values.
Ciphers that are similar to the one specified in the Mark: similar ciphers
field are highlighted in blue.
The darker the shade of blue, the greater the similarity.
The criterion for the fingerprints similarity sets by the K coefficient, 0 is
the zero match, and 1 is a full match.
The default coefficient is 0.8.
The value in the field can be inserted manually or by clicking on the icon at the
end of the set.
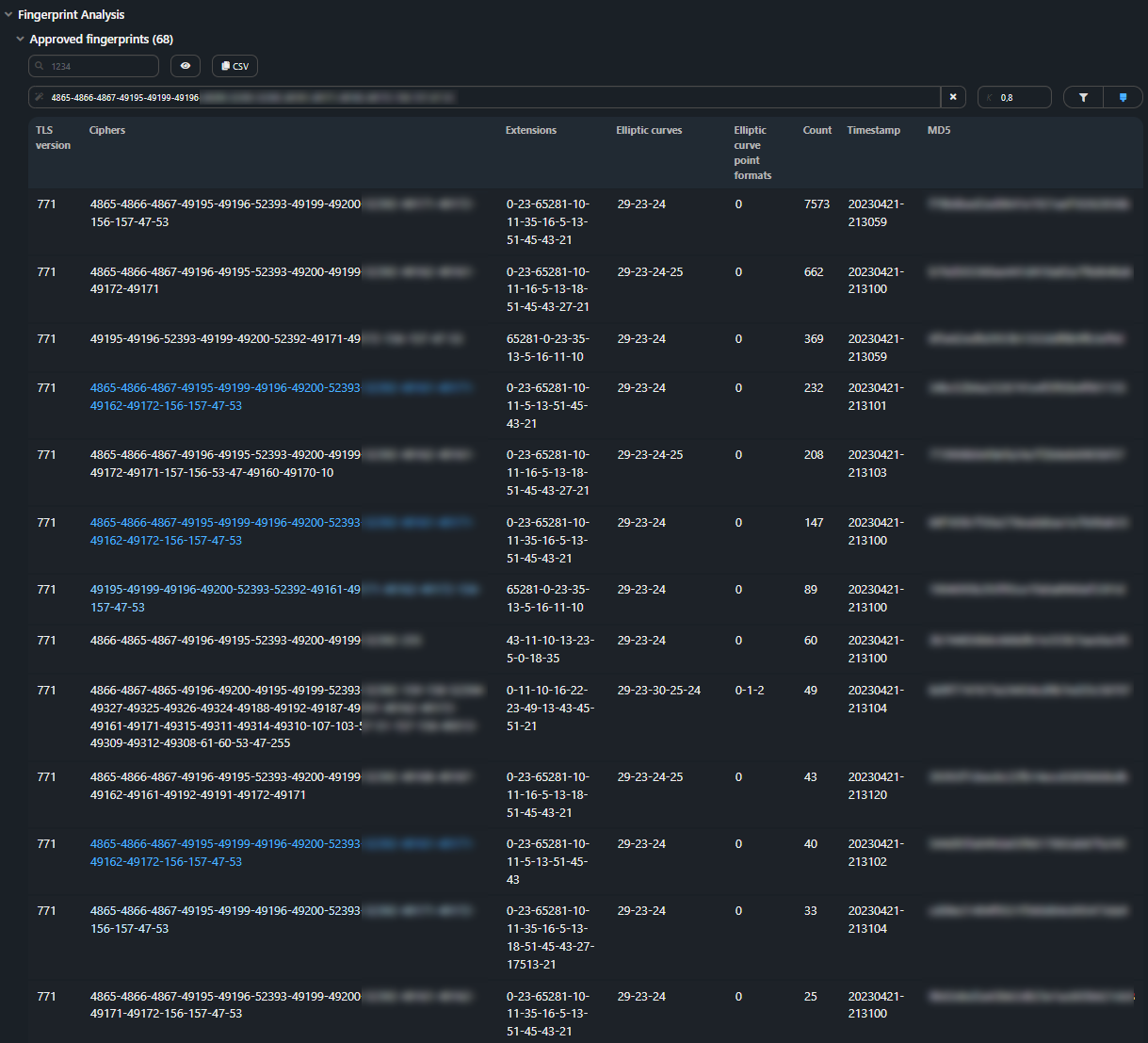
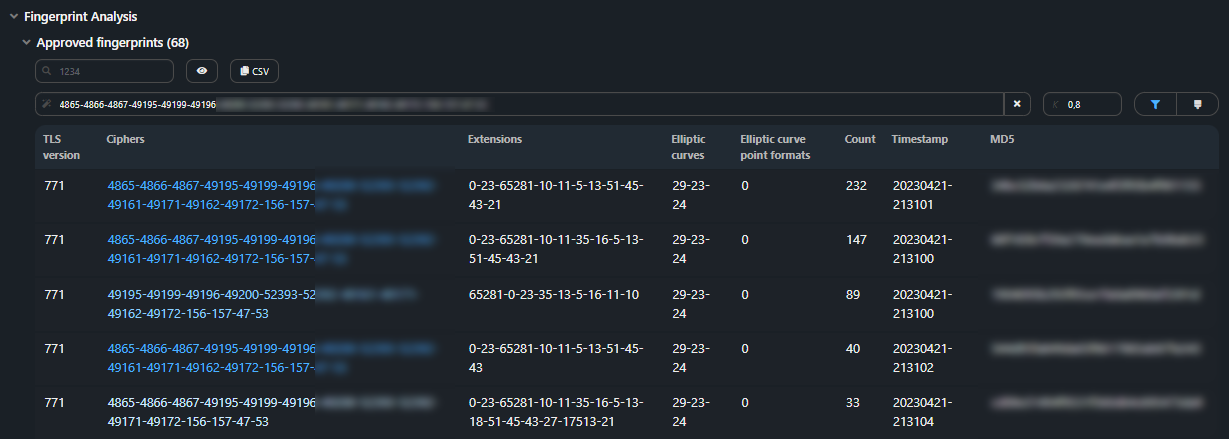
 Press the filter icon to show only similar fingerprints in the table.
Press the filter icon to show only similar fingerprints in the table.

- Fields display turning off;
-
User-Agent by JA3;
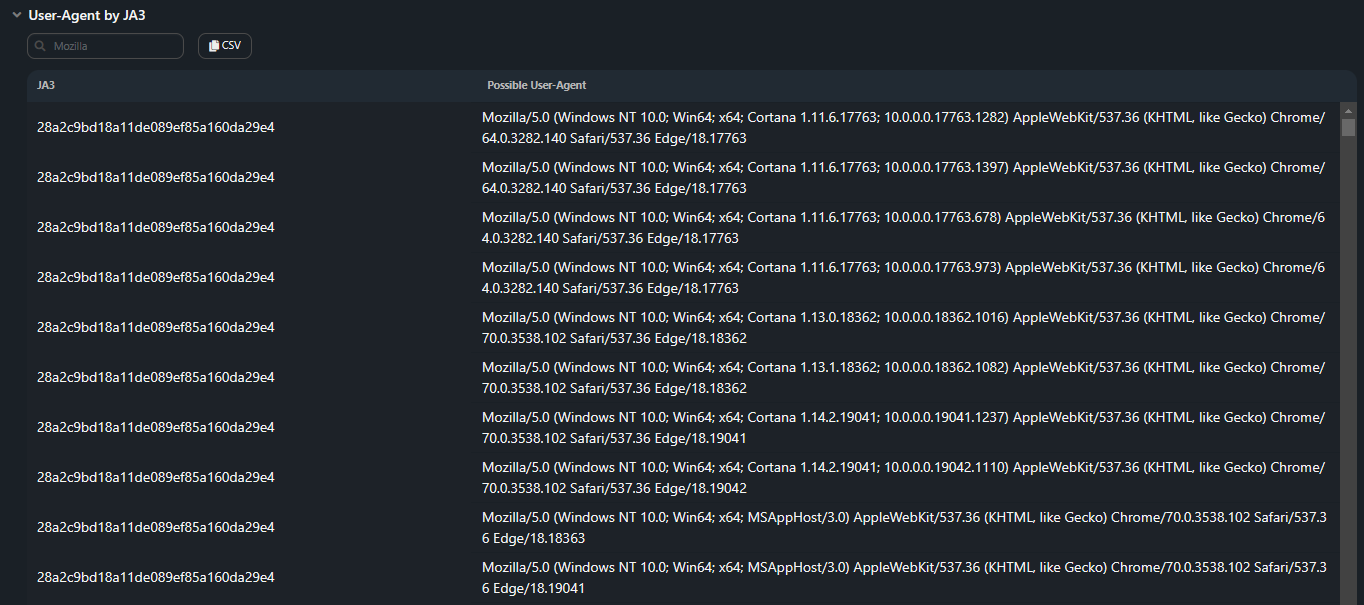
 List of all known User-Agents for each JA3 fingerprint from the dump.
List of all known User-Agents for each JA3 fingerprint from the dump.- JA3 — MD5 Hash JA3-fingerprint for searching information in external sources;
- Possible User-Agent — known User-Agent for this JA3 fingerprint.
-
User-Agent Analysis;
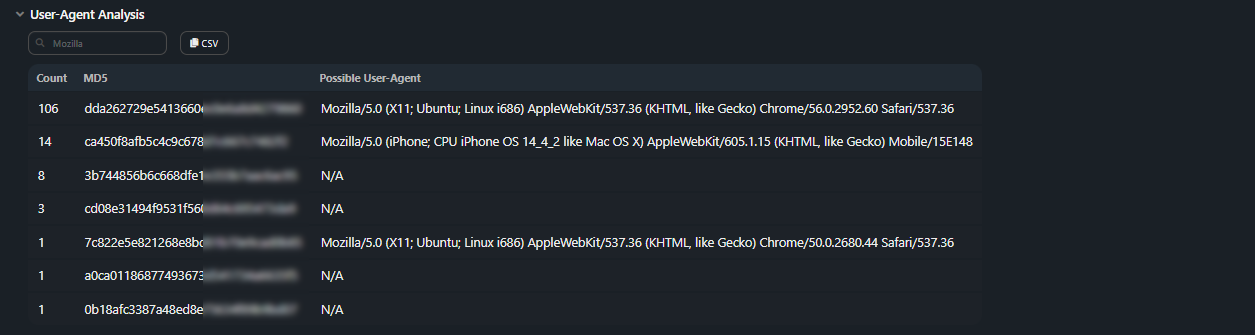
 Additional user intended section.
For each unique fingerprint:
Additional user intended section.
For each unique fingerprint:- Count — how many times the fingerprint is found in the dump;
- JA3 Hash — fingerprint MD5 Hash for comparison with external sources;
- Possible User-Agent — most common User-Agent for this JA3 fingerprint.
-
SNI by name;
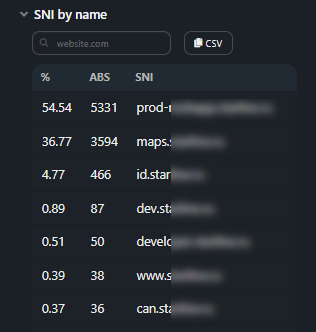
 Section contains the distribution table for a domain name occurrence frequency
in the SNI field:
Section contains the distribution table for a domain name occurrence frequency
in the SNI field:- % — percentage of total SNIs;
- Count — how many times it was observed in the dump;
- SNI — domain name.
-
IPs by SNI;
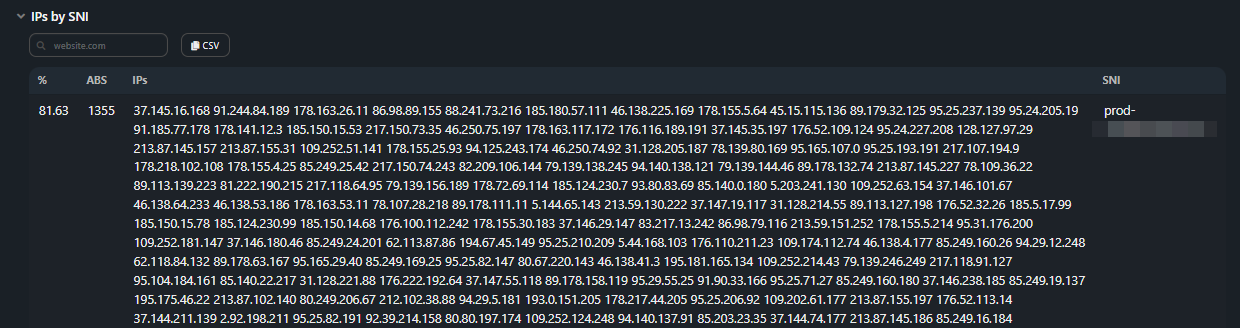
 Section contains the distribution table for unique IPs accessing a specific SNI:
Section contains the distribution table for unique IPs accessing a specific SNI:- % — percentage of total IPs;
- Count — number of IPs;
- IPs — list of IPs;
- SNI — domain name.
-
JA3 by SNI;
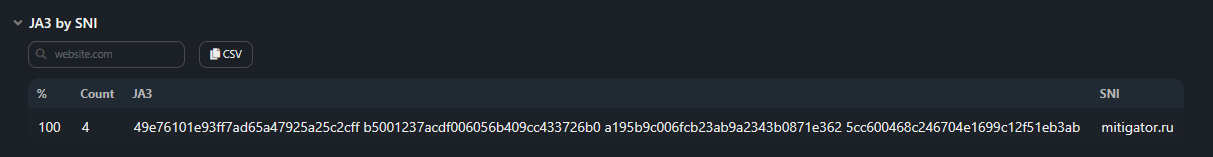
 Section contains the distribution table for the number of unique
JA3 fingerprints that accessed a specific SNI:
Section contains the distribution table for the number of unique
JA3 fingerprints that accessed a specific SNI:- % — percentage of total JA3 fingerprints;
- Count — number of JA3 fingerprints;
- JA3 — list of JA3 fingerprints;
- SNI — domain name.
-
IPs by JA3;

 Section contains the distribution table for unique IPs accessing a specific JA3:
Section contains the distribution table for unique IPs accessing a specific JA3:- % — percentage of total IPs;
- Count — number of IPs;
- IPs — list of IPs;
- JA3 — JA3 fingerprint.
-
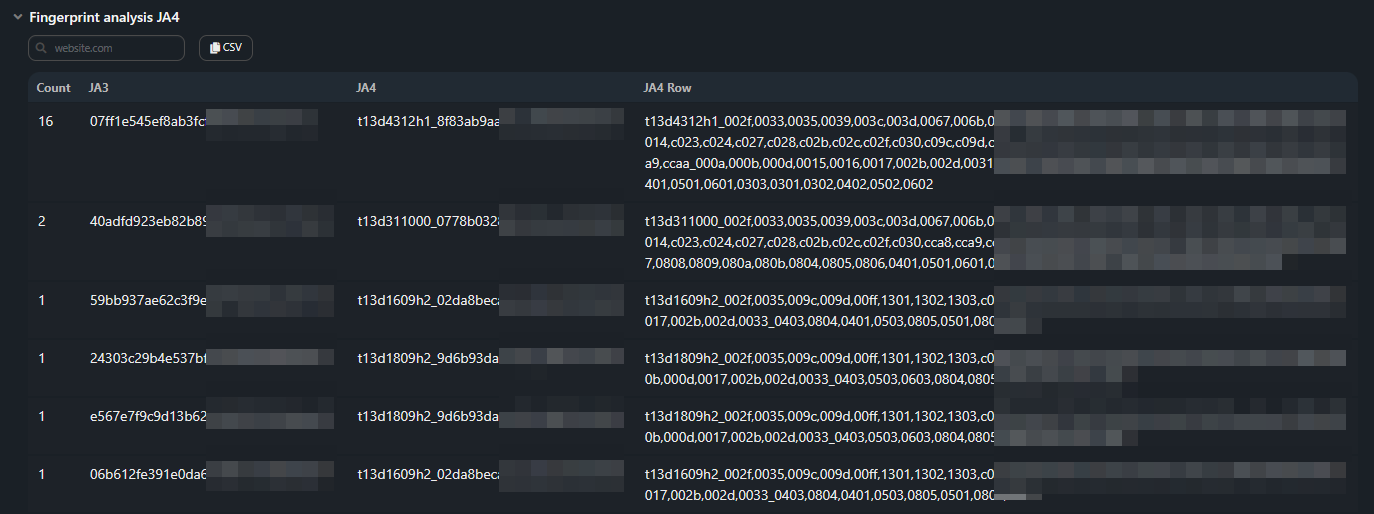
- Count — how many times the fingerprint is found in the dump;
- JA3 — MD5 Hash for JA3 fingerprint;
- JA4 — JA4 fingerprint;
- JA4 Raw — JA4 fingerprint in RAW format.
-
IPs by JA4;
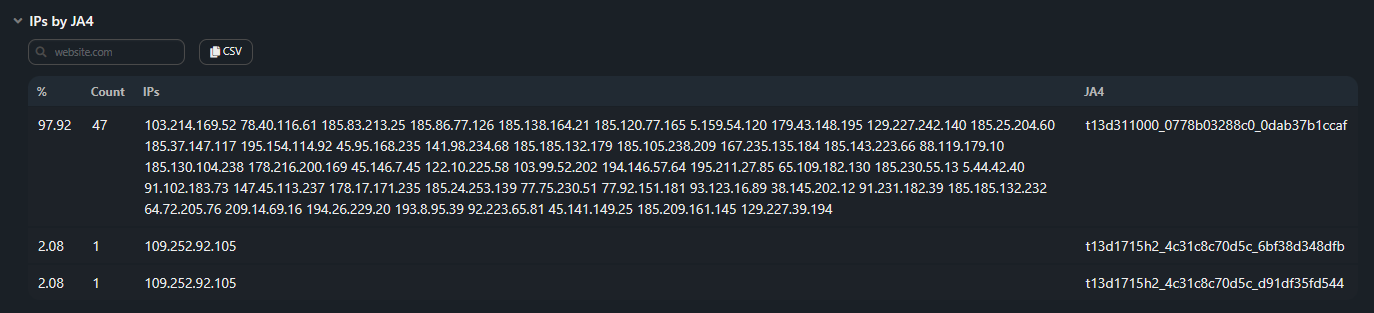
 Section contains the distribution table for unique IPs accessing a specific JA4:
Section contains the distribution table for unique IPs accessing a specific JA4:- % — percentage of total IPs;
- Count — number of IPs;
- IPs — list of IPs;
- JA4 — JA4 fingerprint.
-
JA4 by SNI;
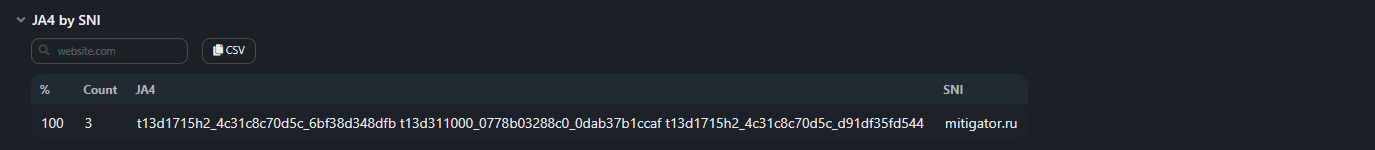
 Section contains the distribution table for JA4 fingerprints occurrence frequency
for each domain:
Section contains the distribution table for JA4 fingerprints occurrence frequency
for each domain:- % — percentage of total JA4 fingerprints;
- Count — number of JA4 fingerprints;
- MD5 — list of JA4 fingerprints;
- SNI — domain name.
-
ClientHello by IPs;
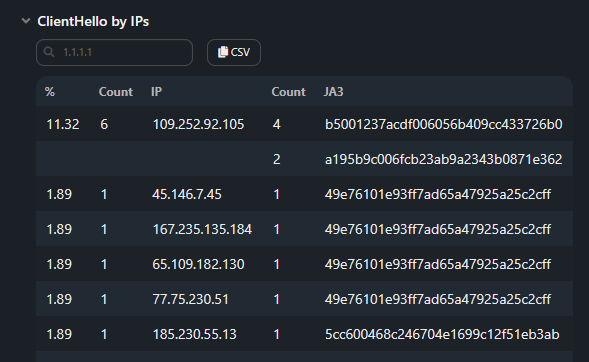
 Section contains the distribution table for ClientHello occurrence frequency
for each source IP:
Section contains the distribution table for ClientHello occurrence frequency
for each source IP:- % — percentage of total ClientHello number;
- Count — number of ClientHellos from IP address;
- IP — IP address;
- Count — how many ClientHellos match a specific JA3 fingerprint;
- JA3 — list of MD5 Hash JA3 fingerprints from this IP address.
-
SS Feed JA3 Lists Analysis;

 Section contains a list of JA3 fingerprints matched the reputation lists:
Section contains a list of JA3 fingerprints matched the reputation lists:- Count — how many times the fingerprint is found in the dump;
- MD5 — fingerprint MD5 Hash for comparison with external sources;
- Comment — comment on the JA3 fingerprint.