MITIGATOR Protection Quick Setup
The information in this article is intended to facilitate understanding of the basic principles of organizing protection using MITIGATOR. Further, as an example, one of the options for setting up the system in the first iteration is given.
Considered situation:
There is an X.X.X.0/24 network and several services running on that network. Of these, we can single out the host Х.Х.Х.100/32, on which we have the site (HTTP, HTTPS) and an application running on proprietary protocols over TCP/7777, UDP/8888.
One of the features of MITIGATOR is the order of traffic processing.
First, all packets are processed in “General protection”, then, using 5-tuple the routing rules distribute traffic according to protection policies. After the protection policies, traffic gets to a couple more countermeasures from “General protection”.
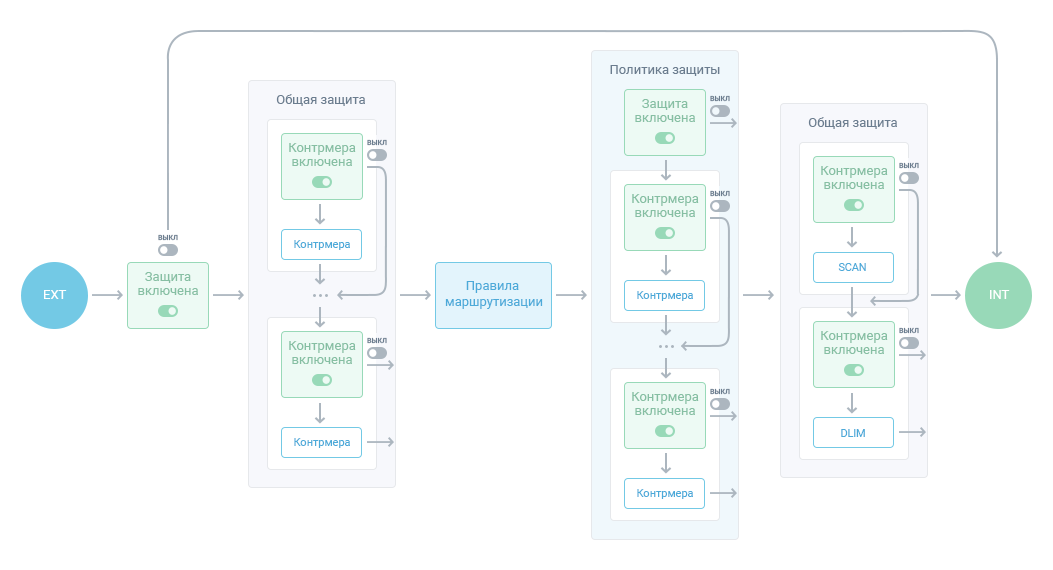
Therefore, you must first configure general protection.
General protection
General protection processes all packets, regardless of whether they belong to any protection policy. General protection is useful when you need to cut traffic off the entire device. For the current task, you will need to configure the ACL and DLIM countermeasures.
ACL
The ACL allows to drop or pass packets according to the header rules for IPv4, IPv6, TCP, UDP, ICMP. In the ACL, you need to register the drop of all initially unnecessary traffic. For example:
# Dropping spoofed packets with our network addresses
drop src X.X.X.0/24
# Dropping traffic from non-routable networks
drop src (0.0.0.0/8 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 127.0.0.0/8 169.254.0.0/16 192.0.2.0/24 198.51.100.0/24 203.0.113.0/24 198.18.0.0/15 224.0.0.0/4 240.0.0.0/4)
# Resetting amplification packets for protocols we do not use
# The list of ports and a description of the amplification protocols can be seen here https://github.com/Phenomite/AMP-Research. Amplification protocols are constantly being added, so the list needs to be updated periodically
drop udp sport (19 6881 389 751 11211 1434 5353 137 111 17 27960 520 1900 27015 7001 3283 5683 37810 2362 30718 502 5351 53413 32414 161 3702 177 17185)
# If no one is playing online games on the network
drop udp sport (27015 30120)
# If the network needs traffic from any NTP and DNS, then we will process it further in the protection policy.
# But in a corporate network, it is enough to allow NTP and DNS traffic only according to the list, for example
pass udp sport 53 src (77.88.8.88 77.88.8.2)
drop udp sport 53
pass udp sport 123 src 194.190.168.1
drop udp sport 123
# Pass only L4 protocols in use: TCP, UDP, ICMP, IPSEC(
pass protocol (1 6 17 50 51 )
# If GRE, IP-IP, L2TP tunnels are used
pass protocol (47 4 115)
# Dropping all other traffic
drop
A hint on the syntax of the rules can be found in the countermeasure help card. The rules are processed in order. If the ACL drops packets outside of the attack, the packet capture card can be used to capture the dropped ACL packets and fine-tune the ACL.
A properly configured ACL eliminates a lot of problems. It is desirable to use such a list at the edge of the network, and it is even better to deal with the upstream and write such rules on the operator’s router.
DLIM
The DLIM countermeasure limits traffic in pps and bps per destination IP address. DLIM processes packets just before exiting MITIGATOR, i.e. after all filtering in general protection and protection policies. DLIM is used to save the network behind MITIGATOR at the cost of partially dumping legitimate traffic coming towards the victim.
Example:
There are 40 servers in a rack, each server is connected via 1GbE to the ToR switch, the ToR switch is connected via 10GbE to the network core. At the same time, the network has 100G of uplinks. If one of the servers is attacked by 25G, and protection is poorly configured for this server, then the ToR link of the switch will be clogged and all 40 servers will be lost. To avoid this, DLIM sets a limit of 1.1G for each address. Thus, at the time of the attack, only 1.1G will reach the ToR switch, and the remaining 39 servers will be saved. In this case, in the absence of an attack, the server will be able to completely utilize its link.
A margin in excess of 1G is needed so that legitimate traffic is not cut off during load bursts due to a limiting error. The error arises due to the peculiarities of counting and specific of traffic passing through the network. A 10% margin is usually excessive, but in the context of this example, there is no task to drop traffic exactly along the border of the server link.
For the current task, let’s assume that each address in the network needs 100 Mbps, except X.X.X.100/32, which can have up to 1 Gbps of legitimate traffic.
When specifying thresholds for X.X.X.0/24, DLIM will decompose the network by /32 and enter thresholds with the same specified values. Then for X.X.X.100/32 we set the threhold separately.
If the user subscribes to notifications by mail, Vestochka or Telegram, he will receive notifications about threshold excession for each /32, which can be used as an additional tool to monitor successful attacks.
Distribution of traffic according to protection policies
Now you need to create protection policies and distribute traffic among them.
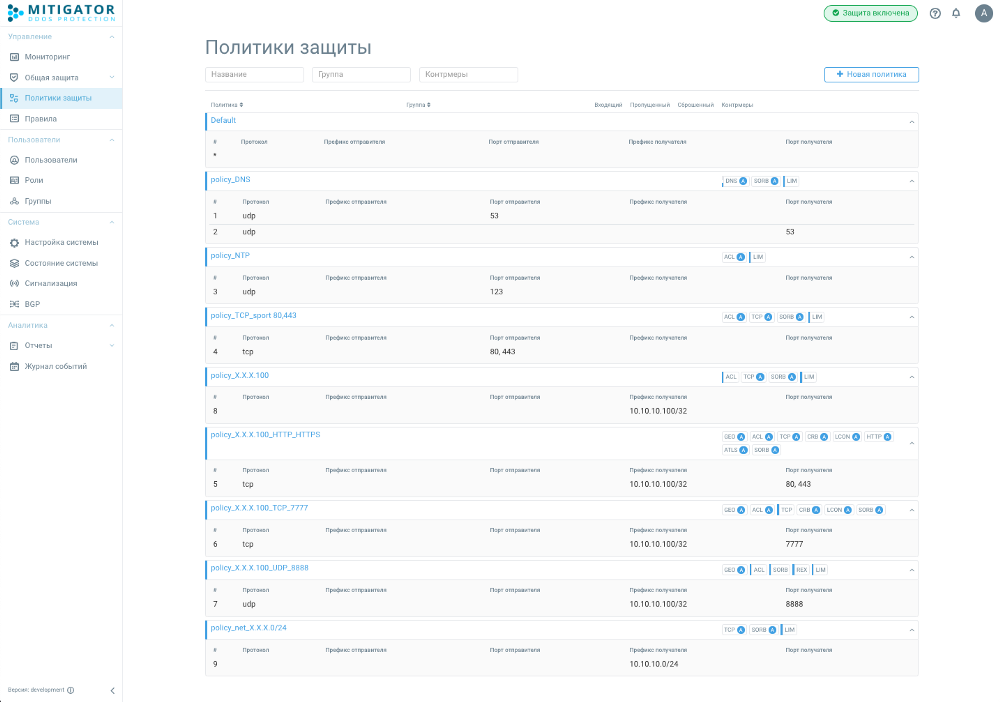
Let’s create the following policies:
policy_DNS
policy_NTP
policy_TCP_sport 80,443
policy_X.X.X.100_HTTP_HTTPS
policy_X.X.X.100_TCP_7777
policy_X.X.X.100_UDP_8888
policy_X.X.X.100
policy_net_X.X.X.0/24
Policy Routing Rules:
1. udp sport 53 -> policy_DNS
2. udp dport 53 -> policy_DNS
3. udp sport 123 -> policy_NTP
4. tcp sport 80, 443 -> policy_TCP_sport 80,443
5. tcp dst X.X.X.100 dport 80, 443 -> policy_X.X.X.100_HTTP_HTTPS
6. tcp dst X.X.X.100 dport 7777-> policy_X.X.X.100_TCP_7777
7. udp dst X.X.X.100 dport 8888 -> policy_X.X.X.100_UDP_8888
8. dst X.X.X.100 -> policy_X.X.X.100
9. dst X.X.X.0/24 -> policy_net_X.X.X.0/24
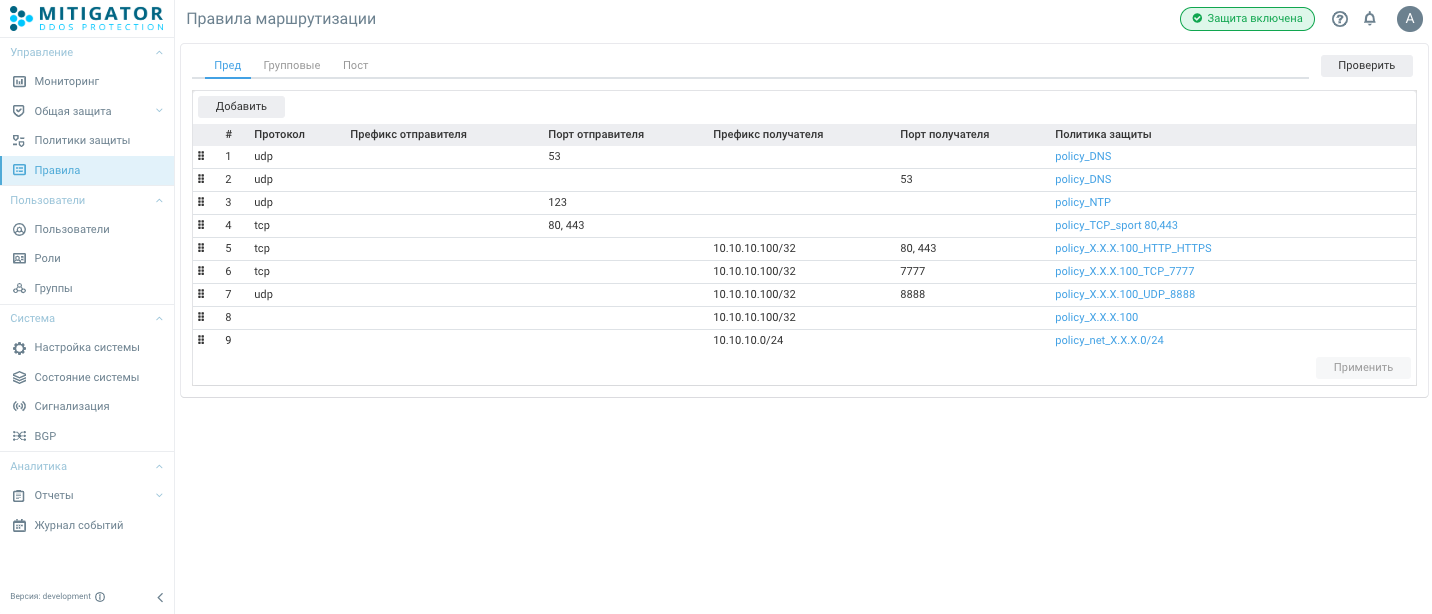
Protection policies setup
Another feature of MITIGATOR is the auto-detection subsystem in protection policies. Autodetection changes the status of a countermeasure when a condition (predicate) is met, or when an anomaly is detected after learning. After installation, MITIGATOR already contains a set of predicates. When setting up a protection policy, the user needs to specify the thresholds for the necessary predicates.
Thresholds have names that characterize the predicate, for example:
ACL.TcpPps.On— threshold for enabling the ACL countermeasure when the rate of packets with TCP segments included in the protection policy is exceeded;GEO.InputBps.Off— GEO countermeasure deactivation threshold when the rate in bps of incoming traffic to the protection policy is reduced;TCP.SYNACKFactor— TCP countermeasure enable threshold if the ratio of SYN to ACK segments is greater than expected.
If necessary, it is possible to create your own predicates through the configuration file.
Through the web interface within the policy, you can also set the “Number of analyzed intervals” and “Number of detected intervals” auto-detection parameters, each interval is 5 seconds. “Number of analyzed intervals” indicates at what time period the values of the predicates are looked up, and the “Number of detected intervals” indicates in how many intervals the predicates must be triggered before changing the status of the countermeasure. By changing these parameters, one can control the reaction speed and detection sensitivity.
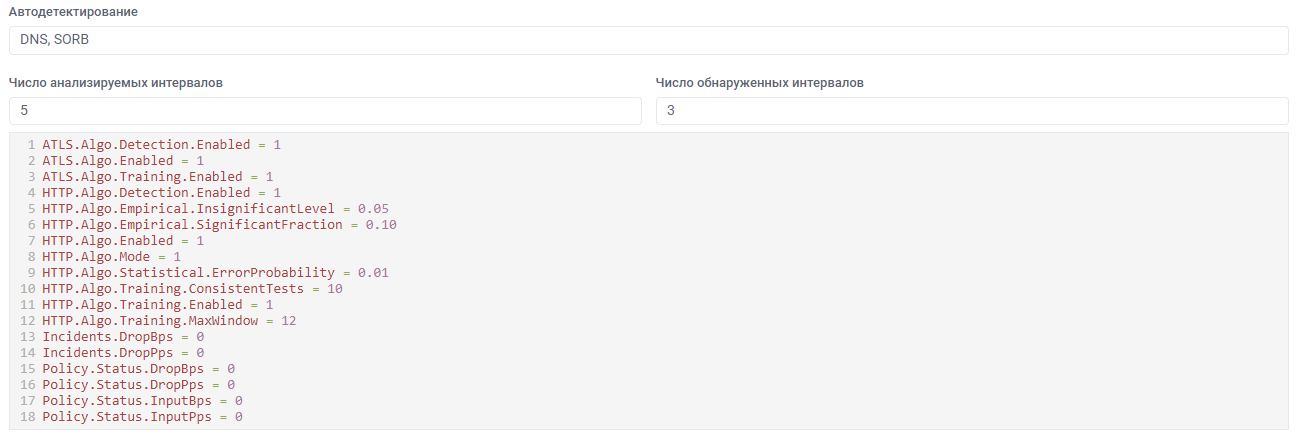
The auto-detection subsystem only enables or disables the countermeasure. The decision to pass or drop the packet is made by the countermeasure itself based on its settings. In this case, the least resource-consuming option is considered, as we do not want to go deep into settings and traffic examination. Therefore, the settings will be far from ideal, but in the general case they will provide protection.
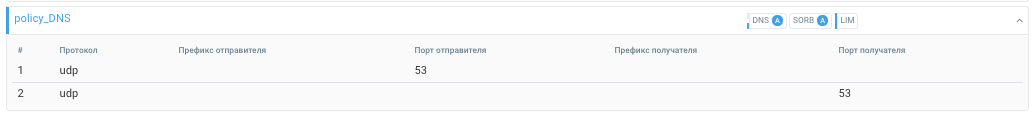
policy_DNS
1. udp sport 53 -> policy_DNS
2. udp dport 53 -> policy_DNS
With rules 1 and 2, we have combined all DNS traffic for the entire network into one policy, including both requests and responses. In the policy, you need to enable DNS and SORB countermeasures in auto-detection mode, and permanently enable LIM.
In the VAL countermeasure, enable the drop of empty UDP packets.
The DNS countermeasure validates the DNS message format and responds to DNS requests.
By DNS.UDP.Rps threshold specify after which amount of DNS requests to enable
the countermeasure.
The countermeasure blocks SORB IP addresses which send traffic that exceeds the thresholds in
pps, bps. Specify SORB.Input.Bps.On threshold to enable the countermeasure,
and SORB.Input.Bps.Off to turn it off.
The LIM countermeasure sets the threshold for traffic that had been passed by the policy in pps and bps. Specify DNS traffic thresholds in LIM countermeasure, above which network traffic becomes undesirable.
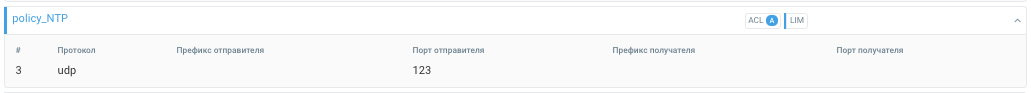
policy_NTP
3. udp sport 123 -> policy_NTP
Rule 3 collected all incoming NTP messages into one policy. In the policy, you need to enable auto-detection for ACL and keep LIM enabled all the time.
Enable the drop of empty UDP packets in the VAL countermeasure.
In case of an NTP Amplification attack, you can set a reset by the size of the responses to getmonlist (440 + 8 + 20) in the ACL:
drop udp len 468
pass dport 123
drop
Set the autodetection thresholds for ACL.Input.Bps.On and ACL.Input.Bps.Off to
enable and disable the ACL countermeasure.
LIM. Set the tresholds in pps, bps.
policy_TCP_sport 80,443
4. tcp sport 80, 443 -> policy_TCP_sport 80,443
Since public web servers are often used for TCP SYN-ACK Reflection, and hosts in the protected network will run to the Internet for updates in some way, it is better to put such traffic into a separate policy using rule 4. ACL, TCP, SORB should be set to autodetection, and LIM enabled constantly.
Rules in ACL:
drop tcp tcp-flags S/SA
drop tcp dport 0–1023
Autodetection thresholds:
ACL.Input.Bps.On, ACL.Input.Bps.Off, ACL.Input.Pps.On, ACL.Input.Pps.Off.
In TCP countermeasure:
Action on SYN+ACK packets: “Check by drop with RST+ACK”; Action on ACK packets: “Check by drop”; Operation time in “Check by drop” mode: 1 minute.
Autodetection thresholds:
TCP.InputPps.On, TCP.InputPps.Off, TCP.InputBps.On, TCP.InputBps.Off,
TCP.AckRate.On, TCP.AckRate.Off, TCP.SynAckRate.On, TCP.SynAckRate.Off,
TCP.RstFloodFactor, Low.Pps, Low.Bps.
Since a predicate based on the ratio of the number of packets (TCP.RstFloodFactor)
is used, the ratio can change greatly at low rates. Therefore, in order to avoid false
positives, it is recommended to set rate thresholds (.Low.), below which autodetection
will not change the status of countermeasures.
Set pps and bps thresholds in the SORB countermeasure. Enable “Add IPs to the temporary block list”.
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
Set pps and bps thresholds in the LIM countermeasure.
policy_X.X.X.100_HTTP_HTTPS
5. tcp dst X.X.X.100 dport 80, 443 -> policy_X.X.X.100_HTTP_HTTPS
Rule 5 diverts traffic from the web server to X.X.X.100. The autodetection policy has ACL, TCP, CRB, LCON, HTTP, ATLS, SORB enabled, and if allowed, GEO.
Rules in ACL:
drop tcp tcp-flags SA/SA
drop tcp sport 0–1023
Autodetection thresholds:
ACL.Input.Bps.On, ACL.Input.Bps.Off, ACL.Input.Pps.On, ACL.Input.Pps.Off.
In TCP countermeasure:
Action on SYN packets: “Check by TCP session drop”; Action on ACK packets: “Check”.
Autodetection thresholds:
TCP.SYNACKFactor, TCP.InputPps.On, TCP.InputPps.Off, TCP.InputBps.On,
TCP.InputBps.Off, TCP.AckRate.On, TCP.AckRate.Off, TCP.RstFloodFactor,
TCP.RstRate.On, TCP.RstRate.Off, Low.Pps, Low.Bps.
In the CRB countermeasure, set the threshold for the creation rate of new TCP connections from the same address. Activate the temporary block list adding function.
Autodetection thresholds:
CRB.SynPps.On, CRB.SynPps.Off.
LCON. Set threshold for simultaneous connections from one address. Activate address blocking.
Autodetection thresholds:
LCON.InputPps.On, LCON.InputPps.Off, LCON.InputBps.On, LCON.InputBps.Off.
HTTP. Choose the appropriate test method, for example, HTML Meta Refresh.
When auto-detection is enabled, learning starts, additional thresholds can be
left unset. If HTTP requests are rare, then it is recommended to set HTTP.Low.Rps
to prevent false positives.
ATLS. Choose operation mode: Active. Other parameters can be changed if the features of the server are known, or to filter a specific attack. When auto-detection is enabled, learning starts, additional thresholds are set according to the situation.
SORB. Set pps and bps thresholds. Activate “Add IPs to the temporary block list”
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
GEO. If service users are geographically localized, and it is acceptable to sacrifice traffic from other regions at the time of the attack, then GEO can be used with detection by missed traffic.
Create a group of countries for which to pass traffic. For example, Russia, Ukraine, Belarus.
Create one or more groups of countries for which to limit traffic. For example, USA and Canada - 10Mbps, 10Kpps, France and Germany - 50Mbps, 50Kpps.
For the rest, specify the default action:: “Drop”.
Autodetection thresholds:
GEO.PassBps.On, GEO.PassBps.Off, GEO.PassPps.On, GEO.PassPps.Off.
Detection by dropped traffic will enable GEO when other countermeasures are not filtering effectively. Enabling GEO will lower the level of passed traffic, which may trigger the GEO disable predicate, causing the increase in missed traffic and enabling GEO again. You can control the cycle by specifying the auto-detection parameters in the “Number of analyzed intervals” and “Number of detected intervals” policies. The larger the “Number of analyzed intervals”, the longer the countermeasure will not be disabled after the traffic level drops below the disable threshold.
policy_X.X.X.100_TCP_7777
6. tcp dst X.X.X.100 dport 7777-> policy_X.X.X.100_TCP_7777
Rule 6 allocates proprietary protocol traffic on host X.X.X.100. ACL, CRB, LCON, SORB, are in autodetection mode, and if allowed, GEO. The required TCP modes of operation are highly dependent on the behavior of the client application. If it is possible to modify the client application, then you need to build in MCR support. If modification is not possible, but the protocol is known, then you can try to create countermeasure within the BPF.
GEO. The same as the policy_X.X.X.100_HTTP_HTTPS.
Autodetection thresholds:
GEO.PassBps.On, GEO.PassBps.Off, GEO.PassPps.On, GEO.PassPps.Off.
Rules in ACL:
drop tcp tcp-flags SA/SA
drop tcp sport 0–1023
Autodetection thresholds:
ACL.Input.Bps.On, ACL.Input.Bps.Off, ACL.Input.Pps.On, ACL.Input.Pps.Off.
In the CRB countermeasure, set the threshold for the rate of creation of new tcp connections from the same address. Activate temporary block list adding function.
Autodetection thresholds:
CRB.SynPps.On, CRB.SynPps.Off.
TCP. You need to test the effect of different TCP countermeasure modes on client traffic. Let’s say that the client application turns out to pass the Action on SYN packets mode well: Check by TCP session drop, but the application server hangs due to a large burst of packets on its port. Which creates a risk that while an attack is being detected, the server will hang. Therefore, the countermeasure must always be kept enabled with the modes:
Action of SYN packets: “Check by TCP session drop”; Action on ACK packets: “Check”.
LCON. Set the threshold for simultaneous connections from one address. Activate address blocking.
Autodetection thresholds:
LCON.InputPps.On, LCON.InputPps.Off, LCON.InputBps.On, LCON.InputBps.Off.
SORB. Set pps and bps thresholds. Activate “Add IPs to the temporary block list”.
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
policy_X.X.X.100_UDP_8888
7. udp dst X.X.X.100 dport 8888 -> policy_X.X.X.100_UDP_8888
The traffic of another critical application at the address X.X.X.100 was directed to the policy by rule 7. Protecting a UDP application can be a very tricky task. Therefore, it is recommended to contact support to discuss the protection scenario of a specific UDP application. MITIGATOR has built-in specialized protection for many UDP applications, but mostly gaming ones. If it is possible to modify the client application, then you need to build in MCR support. If modification is not possible, but the protocol is known, then you can try to create a countermeasure within the BPF.
In general case:
GEO. Similar to the other policies.
Autodetection thresholds:
GEO.PassBps.On, GEO.PassBps.Off, GEO.PassPps.On, GEO.PassPps.Off.
ACL. If a client application is known to establish connections only from a specific port or range, then the rest can be disabled. Otherwise, we should block only system ports.
pass udp sport 8877
drop
or
drop udp sport 0–1023
VAL. Enable drop of empty packets.
SORB. Set pps and bps thresholds. Since address spoofing is possible, the countermeasure may not be effective. Add addresses to TBL according to the situation.
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
REX. If it is possible to template the payload of udp-packets, then set the
traffic signatures: pass (\xDE\xAD\xBE\xEF){3,9}, drop the rest of the packets.
Otherwise, try to block the traffic of a specific attack: drop badbotpayload,
pass other packets.
LIM. In this case, it is necessary to specify the thresholds in LIM, since the probability of attack traffic being missed is high, which will trigger DLIM for the X.X.X.100 address and affect traffic in other policies with this address. The value of the thresholds should be specified to be less than in DLIM.
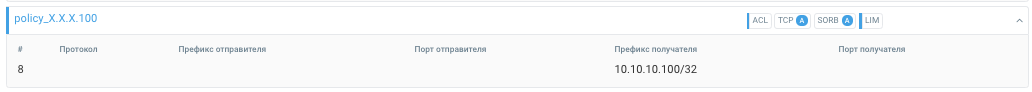
policy_X.X.X.100
8. dst X.X.X.100 -> policy_X.X.X.100
Rule 8 collects the remaining traffic for host X.X.X.100. TCP and SORB are set to autodetection, ACL and LIM - to be always active.
ACL. Specify what other packets are expected on this host. If no connections are expected from the Internet to other ports, then drop the SYN.
drop tcp tcp-flags S/SA
drop tcp dport 0–1023
drop udp dport 0–1023
pass icmp icmp-type (0 3 8 11)
TCP:
Action on SYN+ACK packets: “Check by drop with sending RST+ACK”; Action on ACK packets: “Check by drop”; Operation time in the “Check by drop” mode: 1 minute.
Autodetection thresholds:
TCP.InputPps.On, TCP.InputPps.Off, TCP.InputBps.On, TCP.InputBps.Off,
TCP.AckRate.On, TCP.AckRate.Off, TCP.SynAckRate.On, TCP.SynAckRate.Off,
TCP.RstFloodFactor, Low.Pps, Low.Bps.
Set pps and bps thresholds in the SORB countermeasure. Activate “Add IPs to the temporary block list”.
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
Set pps and bps thresholds in the LIM countermeasure.
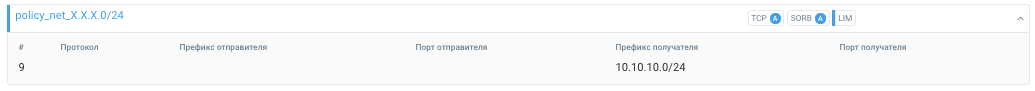
policy_net_X.X.X.0/24
9. dst X.X.X.0/24 -> policy_net_X.X.X.0/24
The last rule collects all the remaining network traffic. You should try to make
sure that there is no traffic in the Default policy. When describing the next services,
you will need to add rules before this rule. Since we know little about the traffic
in this policy, we make very coarse settings. TCP, SORB are in autodetection and LIM
permanently active.
VAL. Activate all additional modes.
TCP:
Action on SYN packets: “Check by TCP sesion drop”; Action on SYN + ACK packets: “Check by drop”; Operation time in the “Check by drop” mode: 1 minute.
Autodetection thresholds:
TCP.AckRate.On, TCP.AckRate.Off, TCP.SynAckRate.On, TCP.SynAckRate.Off,
TCP.RstFloodFactor, TCP.SynRate.On, TCP.SynRate.Off, TCP.SYNACKFactor,
TCP.Low.Pps, TCP.Low.Bps, TCP.InputPps.On, TCP.InputPps.Off, TCP.InputBps.On,
TCP.InputBps.Off.
SORВ. Set pps and bps thresholds. Activate “Add IPs to the temporary block list”.
Autodetection thresholds:
SORB.Input.Bps.On, SORB.Input.Bps.Off, SORB.Input.Pps.On, SORB.Input.Pps.Off.
LIM. Since the policy is poorly configured, the attack on all network addresses at once is possible, yet there may not be an excess in DLIM for each host. This can cause a failure of the devices behind. Therefore, it is necessary to limit the total outcoming traffic to the internal network.
Set pps and bps thresholds in LIM countermeasure bordering the performance of MITIGATOR devices located behind.
Additionally, it is recommended to change the
Policy.Status.DropBps, Policy.Status.DropPps, Policy.Status.InputPps,
Policy.Status.InputBps threshold values in each protection policy. Then the
color indication of policy statuses in the list of policies will be more adequate.
You also need to configure automatic packet capture with email delivery.
To do this, you need to register a mail server in the system settings, and set
the capture parameters in the “Packet capture” card and specify the PCAP.* thresholds.
This is useful if the attack was successful and you need to adjust the protection.
Conclusion
This article provides an example that allows you to highlight the basic approach to setting up the MITIGATOR.
Detailed information about the operation of specific countermeasures is provided in the built-in help in MITIGATOR.
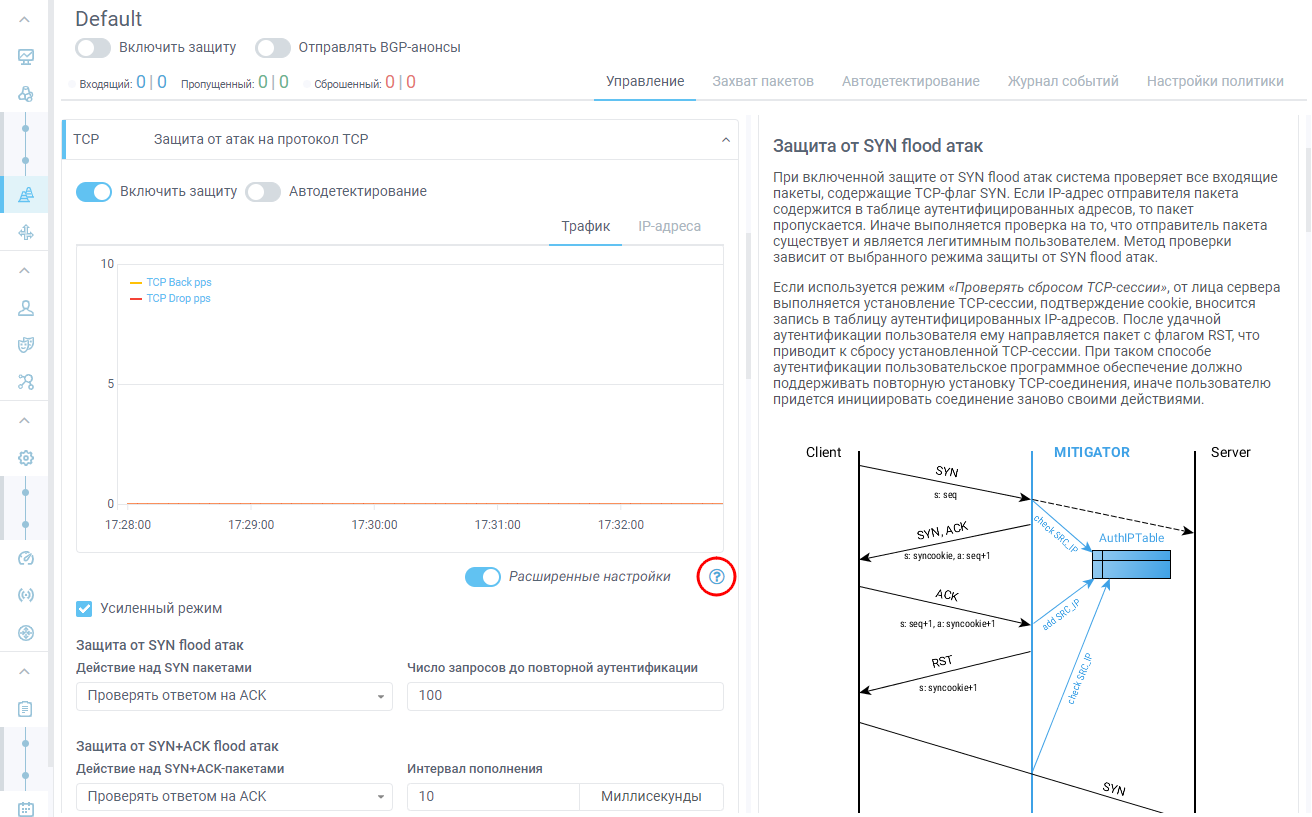
In any networking scenario, it is recommended to use BGP where possible to route traffic to the MITIGATOR, even if you plan to always route traffic through it. This option gives more flexibility in setting up protection and improves fault tolerance.