Version 23.02
Version v23.02 adds an Host Protection Detector, a new ACLI countermeasure,
JA3 named lists, FHRP
support in “Common LAN” integration mode, support for GeoIP2 databases.
The functionality of Collector and PCAP, as well as ATLS, DTLS, JA3, TBL,
TBL6, RETR, RETR6, VAL, VAL6, DNS, WL, WL6 countermeasures has been expanded.
Changes in v23.02
HPD. “Host Protection Detector” has been added.
For the situation when traffic of many dst IPs is sent to the protection policy and it is necessary to activate filtering only for traffic of the addresses under attack, the “Host Protection Detector” (HPD) mechanism has been added. The mechanism allows the activation of filtering in individual countermeasures only for IP addresses whose traffic exceeds the set threshold in packets or bits.
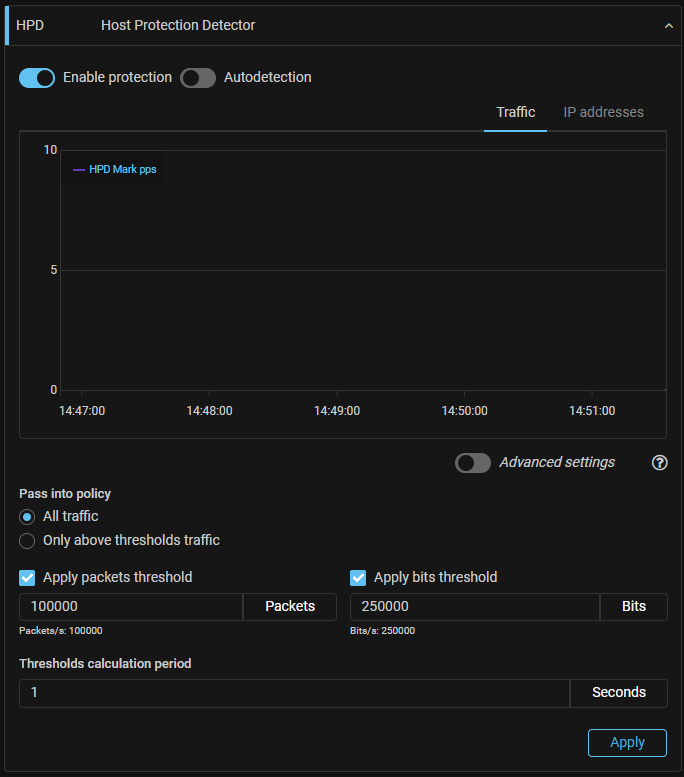
Depending on the selected detector operation mode, the following traffic be sent for processing by policies’ countermeasures:
- all traffic of the protection policy;
- only traffic of the addresses for which the threshold is exceeded. The rest of the traffic will be passed to the policy output without processing.
Policy countermeasures can process the traffic independently according to the specific host protection settings if all traffic is sent to the policy.
When the threshold has been exceeded, a corresponding entry is generated in the event log. The user can be notified of the detector triggering event if notification channels for system events is configured.
Prefixes lists and FlowSpec rules lists for announcement over BGP can be formed
based on HPD data. The names of such lists contain the .hpd. suffix.
HPD is compatible with the auto-detection mechanism and host protection in TCP
and MINE countermeasures (HPA).
HPD is supported in the following policy countermeasures:
BL, TBL, ACL, GEO, RTS, SOUR, RETR, TCP, MINE, CRB, LCON, SLOB, HTTP, ATLS, JA3,
DTLS, GAME, WG, DNS, SIP, SPLI, FRB, SERB, SORB, SPRB, REX, BPF, USF, NCL, LIM.
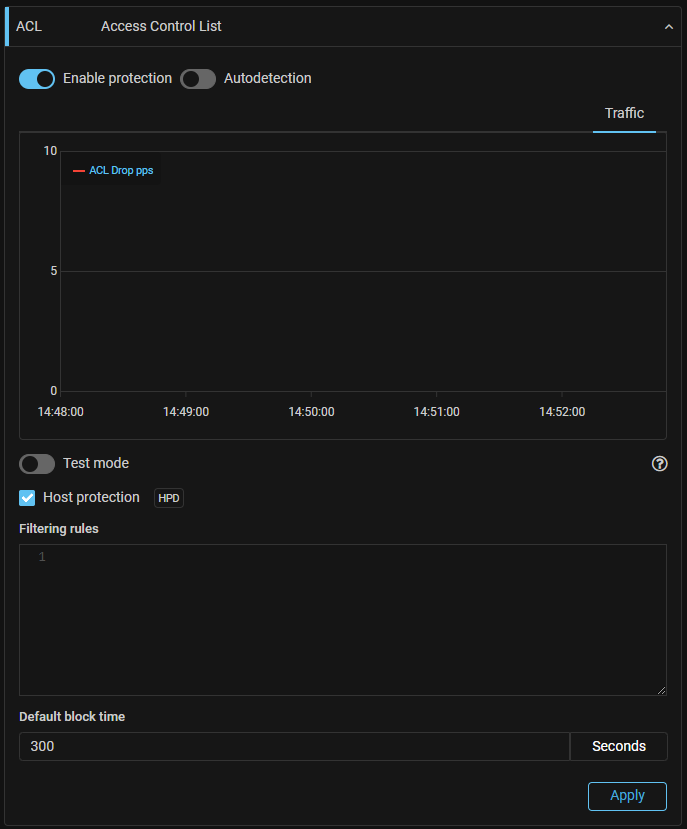
ACLI. New “Internal Network Traffic Access Control List” countermeasure has been added to the general IPv4 protection.
The countermeasure filters traffic coming from the internal network. It is similar
in operation and syntax to the ACL countermeasure, but does not support the block
action.
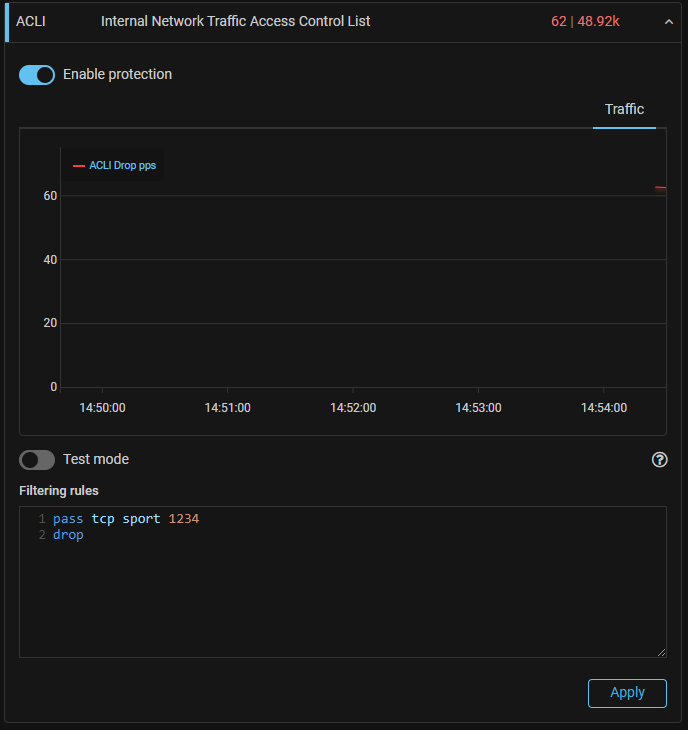
MITIGATOR can be used now as a bidirectional and high performance stateless firewall with a large rule set.
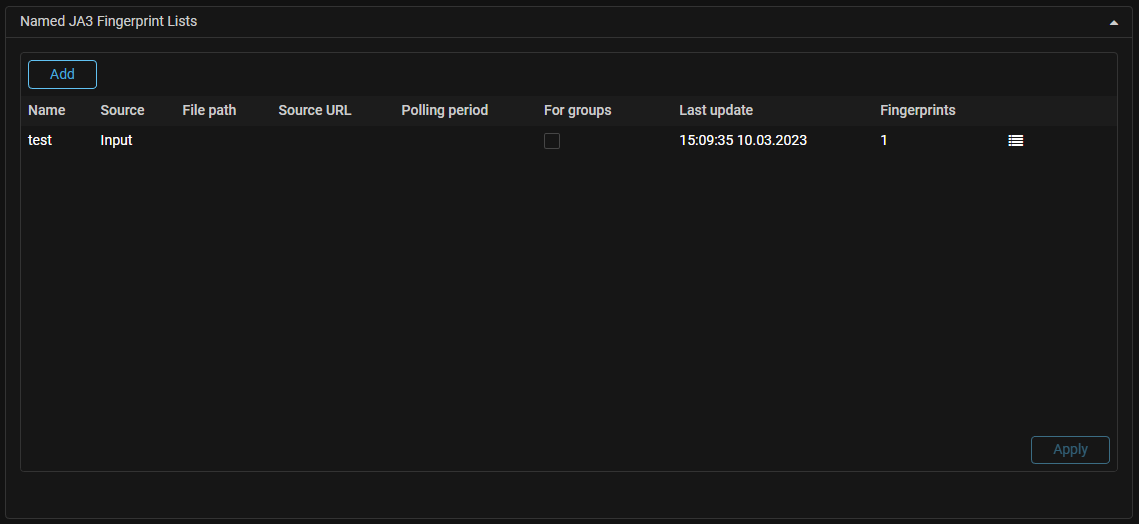
JA3Lists. Named lists of JA3 fingerprints have been added.
It is now possible to set named lists of JA3 fingerprints in the system settings.
The operation logic and value sources are the same as for named lists of IP addresses.
JA3 named lists can be used in ATLS, DTLS, JA3 countermeasures, and in PCAP
for filtering.
Import of feeds made by the MITIGATOR team is supported with a token.
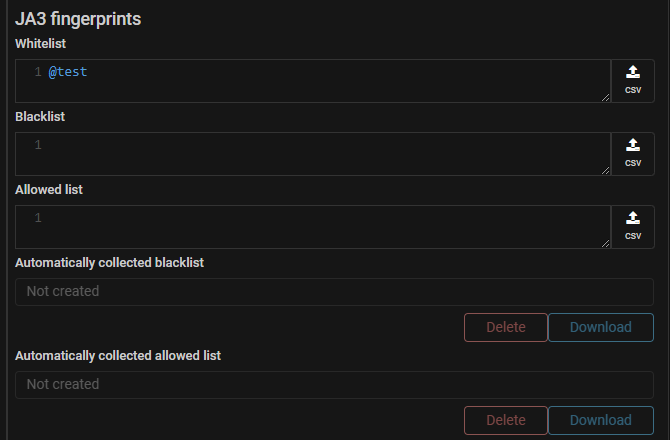
ATLS. Support for JA3 named lists has been added.
The ATLS countermeasure now uses an input field to specify the white list,
black list, and allowed list, where you can specify a named list of
JA3 fingerprints. The ability to load the file remains.
When a file is loaded, its contents are added to the current values
and displayed in the input field.
DTLS. Support for JA3 named lists has been added.
You can now specify a named list of JA3 fingerprints in the countermeasure for the whitelist, blacklist, and allowed list.
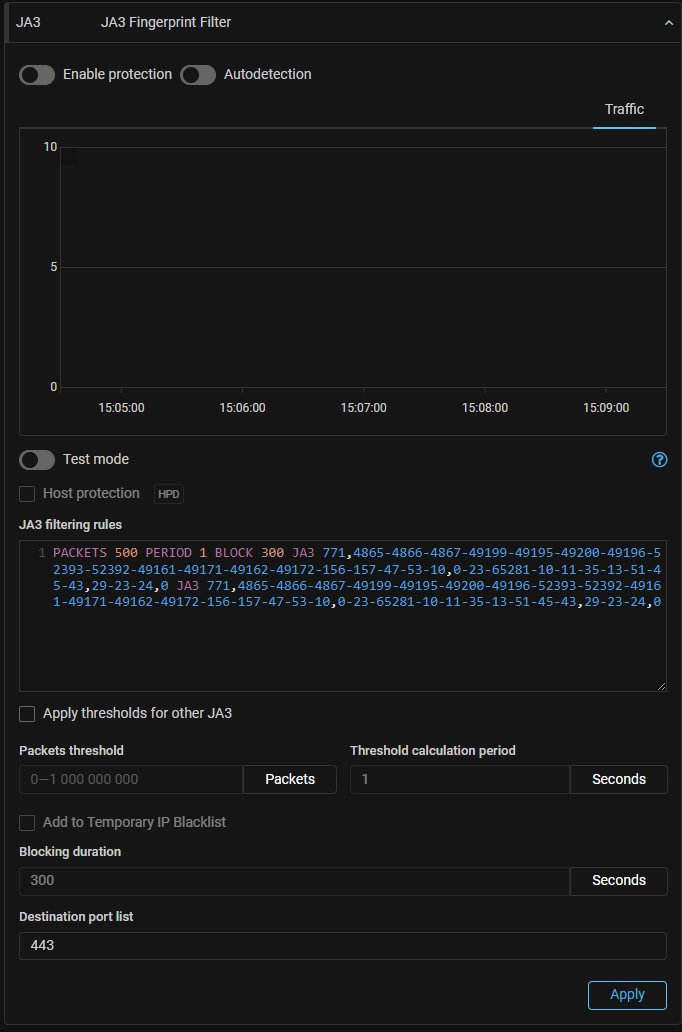
JA3. Support for JA3 named lists has been added.
JA3. The ability to specify more than one JA3 fingerprint in a rule has been added.
Each fingerprint must be preceded by the JA3 keyword. A logical “OR” is applied between fingerprints.
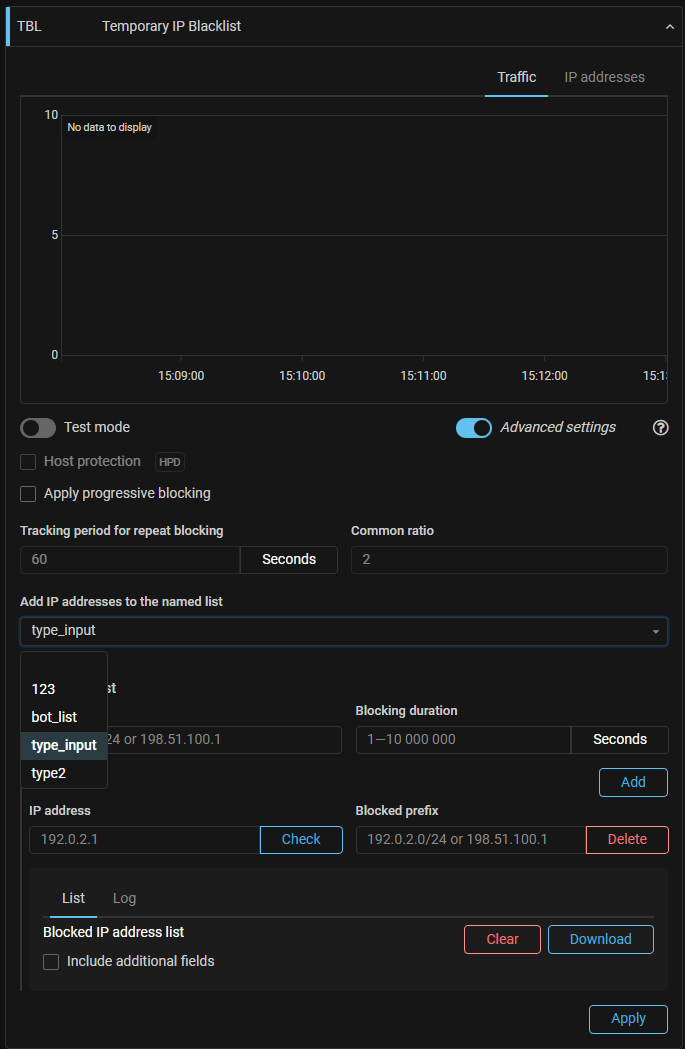
TBL. A mechanism for filling the named list with blocked IP addresses has been added.
Now you can select a named list in TBL, which will be filled with the blocked IP addresses values. Thus, it is possible to fill a named list with data from several TBLs and use it in other countermeasures and policies.
TBL. The way the countermeasure names are displayed in the TBL log has been changed.
The TBL block log now displays the countermeasure short name instead of the full name.
TBL6. A mechanism for filling the named list with blocked IP addresses has been added.
TBL6. The way the countermeasure names are displayed in the TBL6 log has been changed.
RETR. BYPASS action has been added.
Sometimes it may be necessary to exclude the effect of a countermeasure on traffic
that matches a certain pattern, so a BYPASS action without thresholds has been
added. Traffic that matches the pattern in such rule is passed to the countermeasure
output, and the sender’s IP address is not entered in the authenticated table.
RETR6. BYPASS action has been added.
VAL. New drop options have been added:
The countermeasure can now drop:
- TCP segments with the ACK flag and the same Sequence and Acknowledgment numbers;
- Packets that specify reserved bits in the TCP header as defined in RFC 9293.
Both options are enabled by default.
VAL6. New drop options similar to those in VAL have been added.
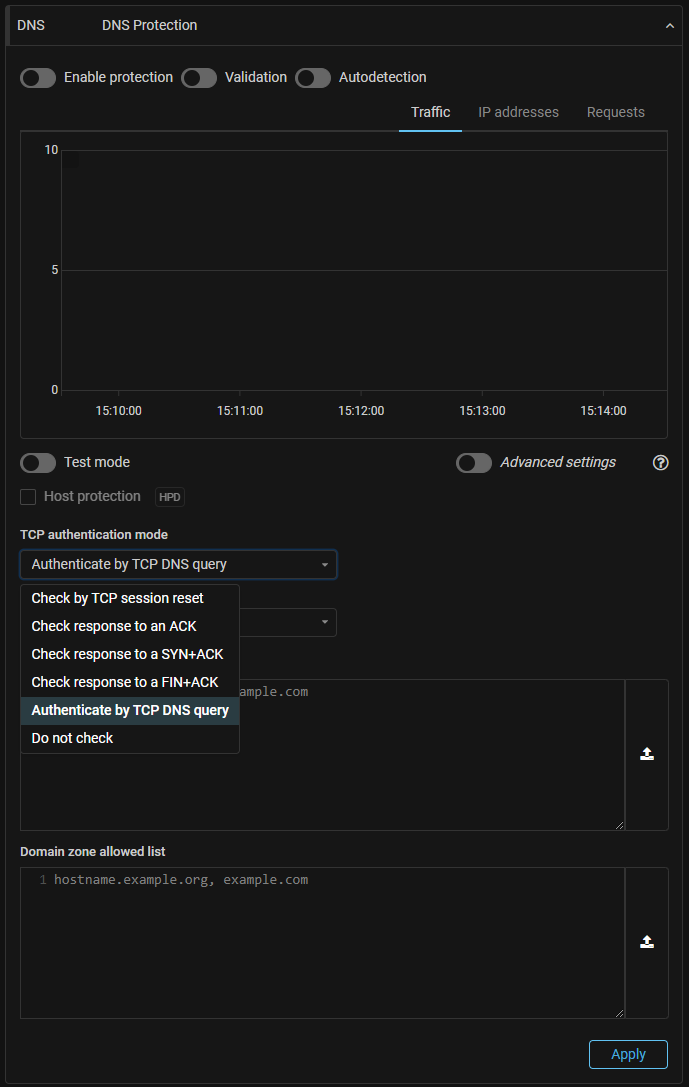
DNS. A new TCP authentication mode has been added.
WL. The ability to pass traffic past the BL countermeasure has been added.
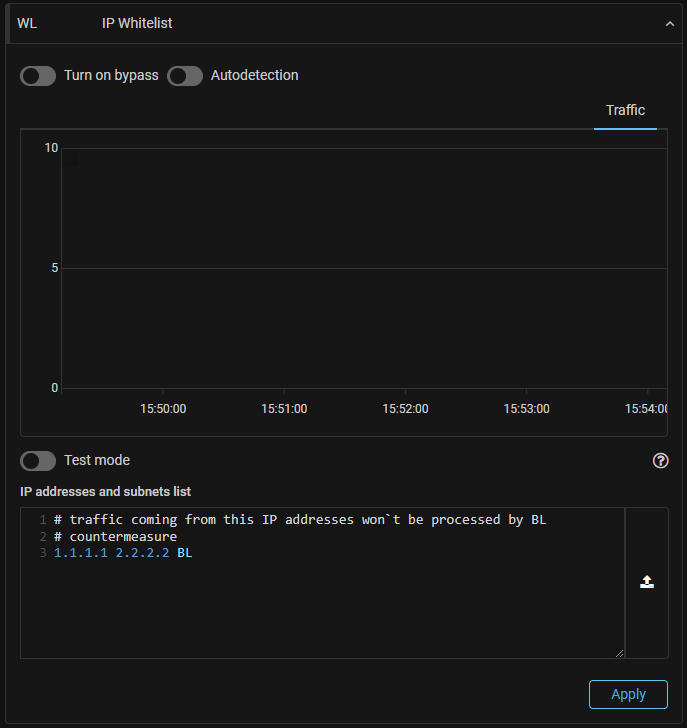
WL. The ability to pass a packet without being processed by specific countermeasures only has been added to general IPv4 protection, similar to a protection policy.
WL6. The ability to pass traffic past the BL6 countermeasure has been added.
WL6. The ability to pass a packet without being processed by specific countermeasures only has been added to general IPv6 protection, similar to a protection policy.
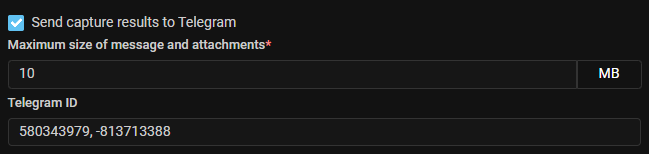
PCAP. The ability to specify multiple Telegram IDs in autocapture has been added.
PCAP. Information about sFlow settings has been added.
Now the capture file comment specifies the sFlow generation settings.
PCAP. Indication of start time and duration of capture has been added.
The capture start time and its duration are displayed now after starting the capture, opposite of the “Capture packets” header.
PCAP. Support for named lists of JA3 fingerprints in the filter field has been added.
PCAP. Merging of capture files from different instances has been added.
The “Merge capture results from all instances into one file” flag has been added for the convenience of packets capture in a cluster with many instances. If the flag is set, then the captured packets from all cluster instances within the selected capture point are combined into a single file. The package comment contains the ID and name of the instance on which it was captured.
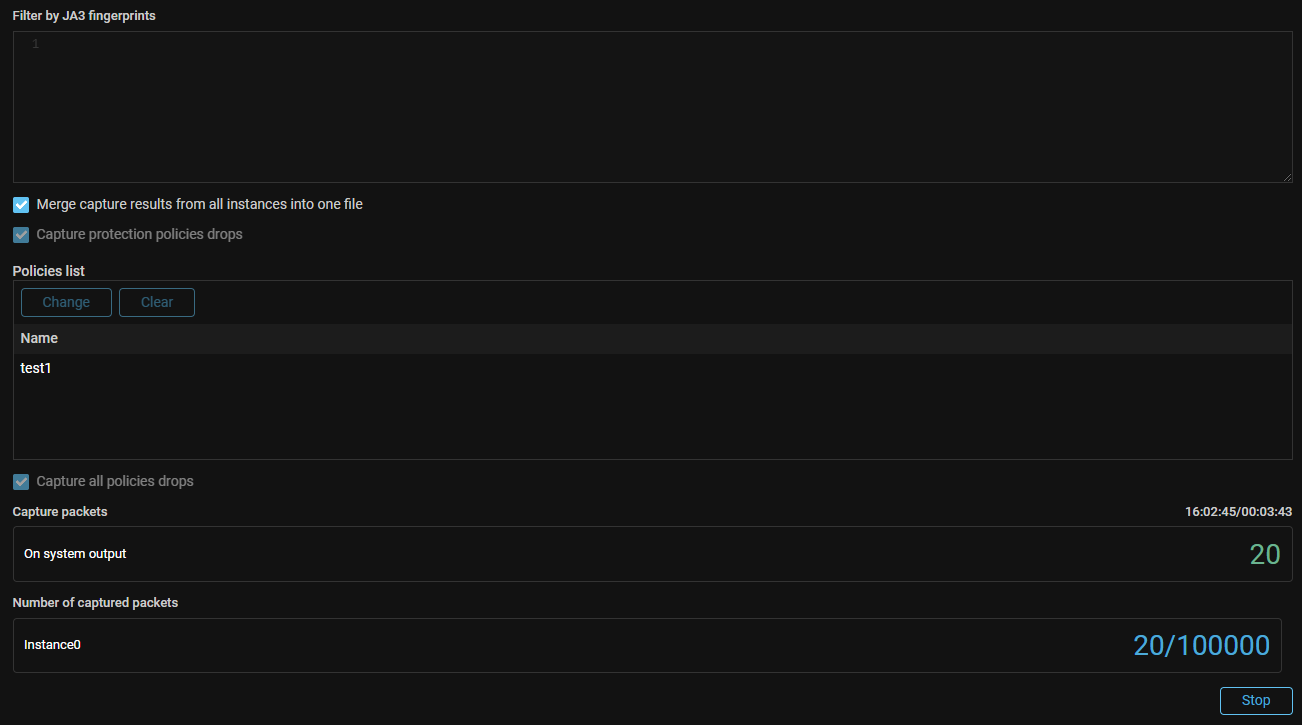
PCAP. The ability to capture policy drops in general protection has been added.
Now you can specify a list of protection policies which dropped packets will be included in the resulting file when capturing “Dropped” packets in general protection. The packets dropped in all protection policies, not only in the specified ones, will be captured If the “Capture all policies drops” checkbox is set.
GeoIP. GeoIP2 databases support has been added.
GeoIP.
The ability to load Geo bases in .mmdb format has been added.
Collector. Display of statistics from Collector for all protection policies has been added.
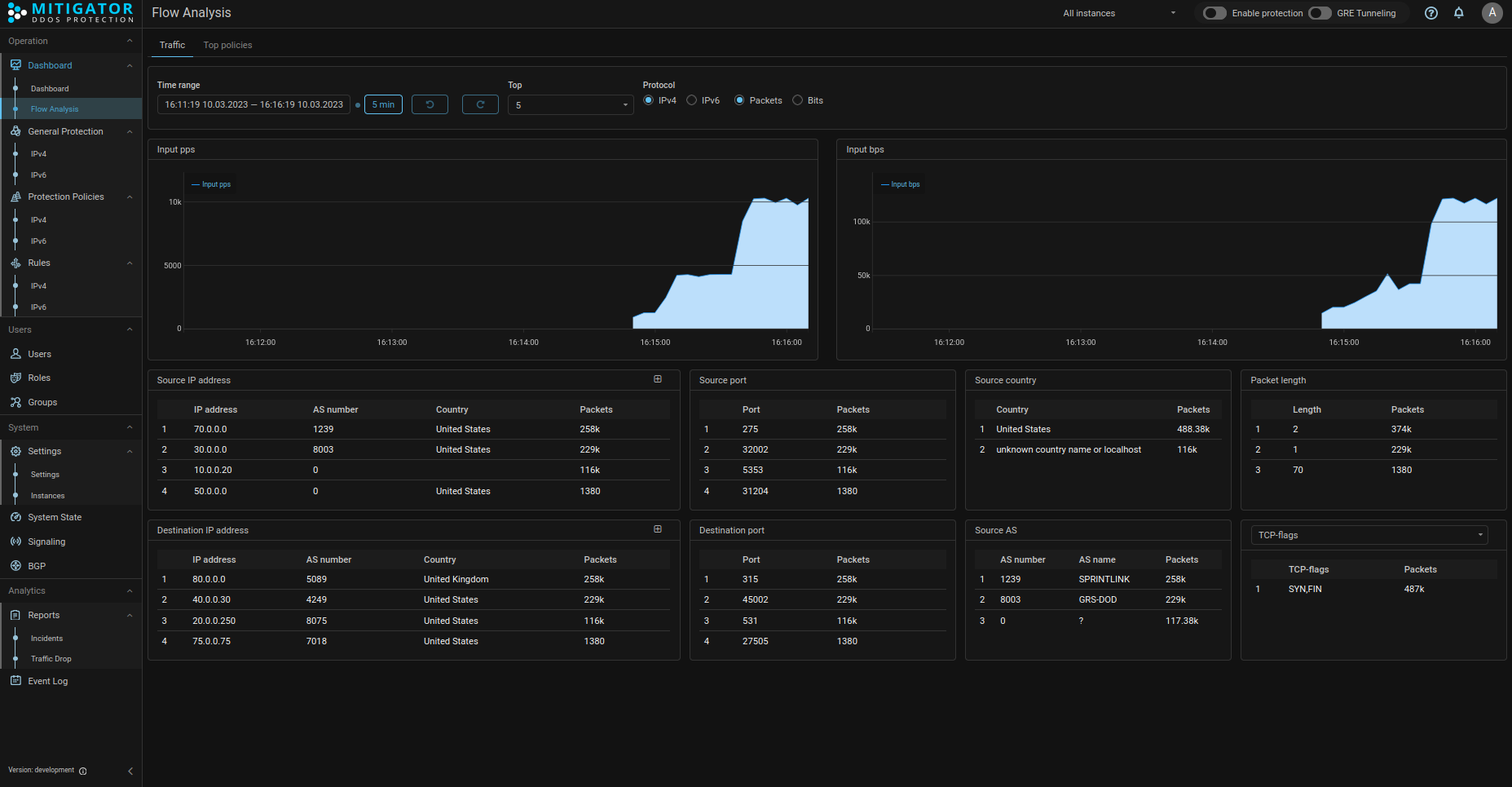
A new “Flow Analysis” interface page has been added. It displays data in the form of traffic graphs and statistics tables grouped by various criteria, similar to the “Flow Analysis” tab of specific policies.
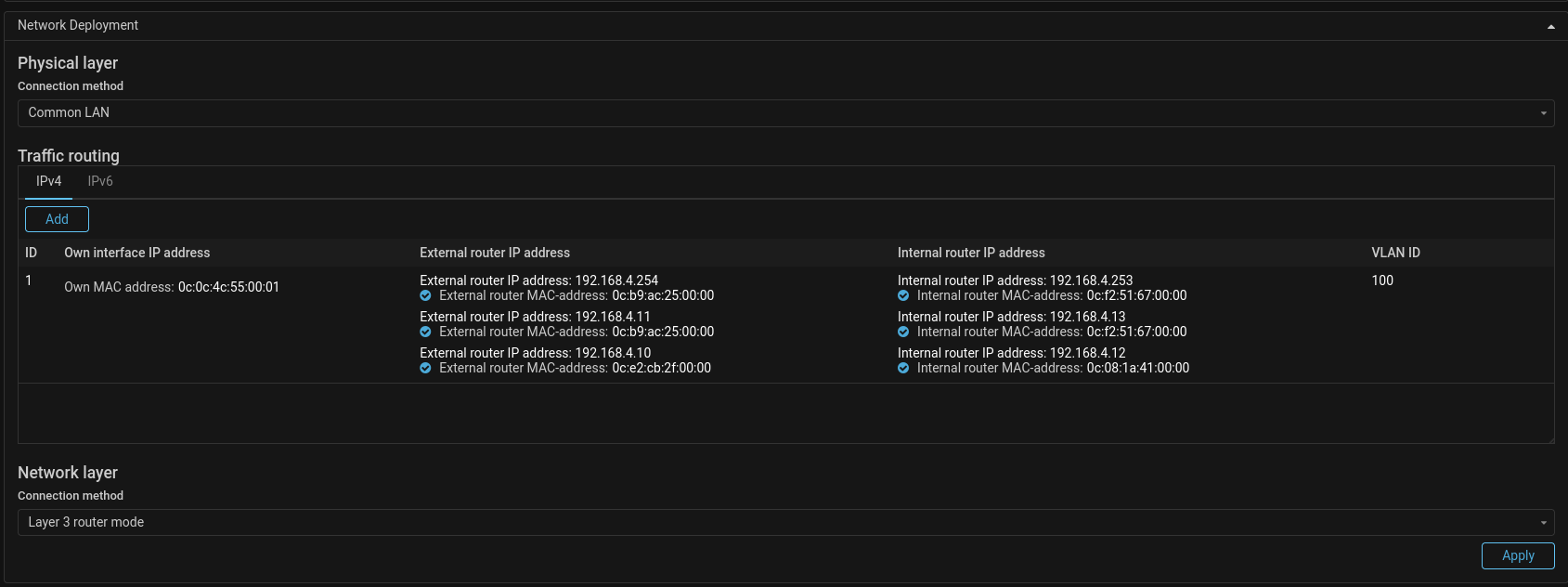
Deploy. FHRP support for “Common LAN” deployment mode has been added.
To determine the real MAC addresses of external or internal routers their real IP addresses should be specified in settings instead of the virtual one. But if frames from all FHRP devices arrive with a virtual MAC address, it is sufficient to specify only the virtual IP address.
UX. Display of information about the number of system instances in the cluster has been added.
The “License” card on the “Instance” page now displays how many system instances are used by this cluster out of the total number of licensed instances.
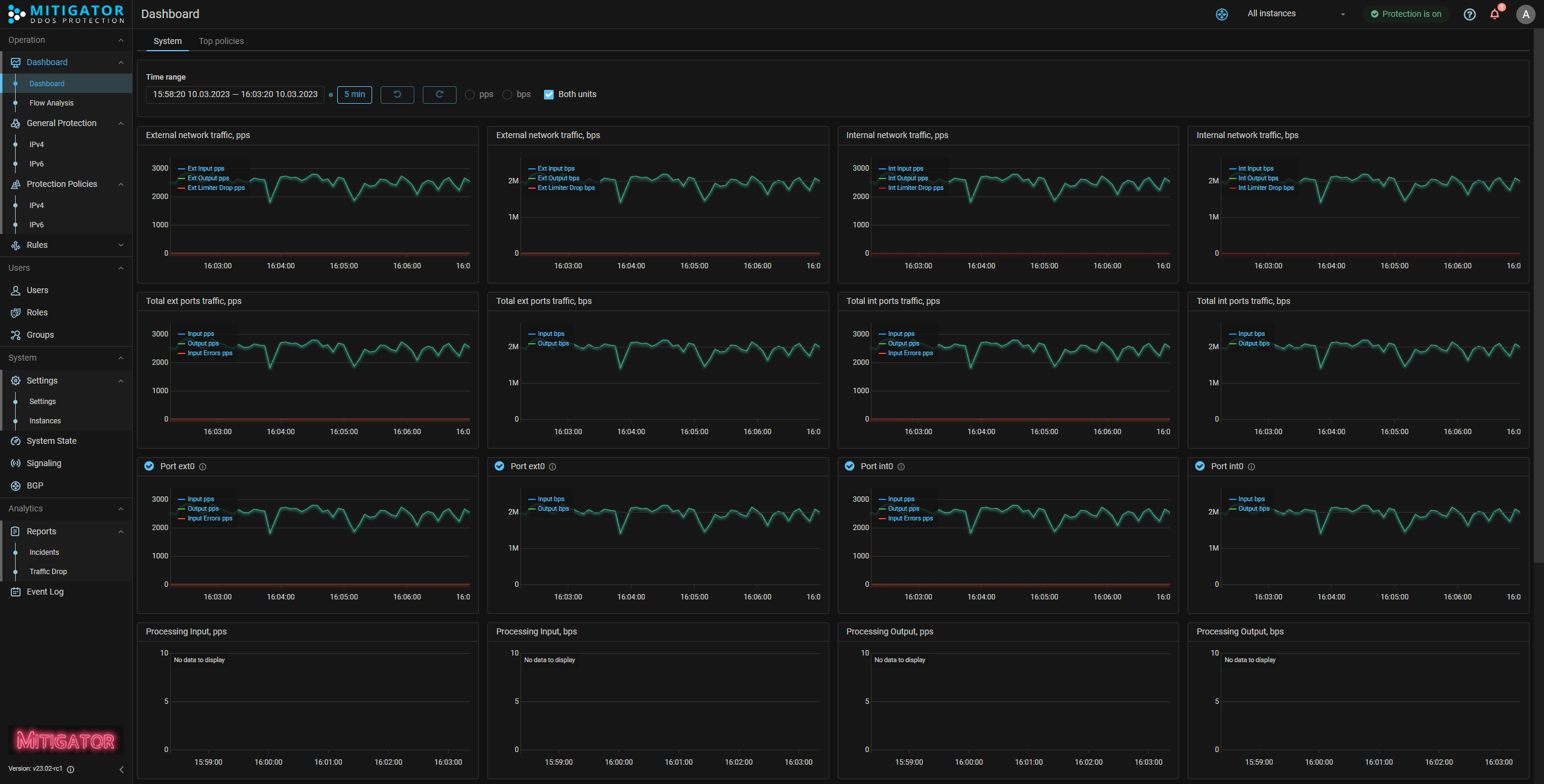
UX. Mode for simultaneous displaying in pps and bps of Dashboard graphs has been added.
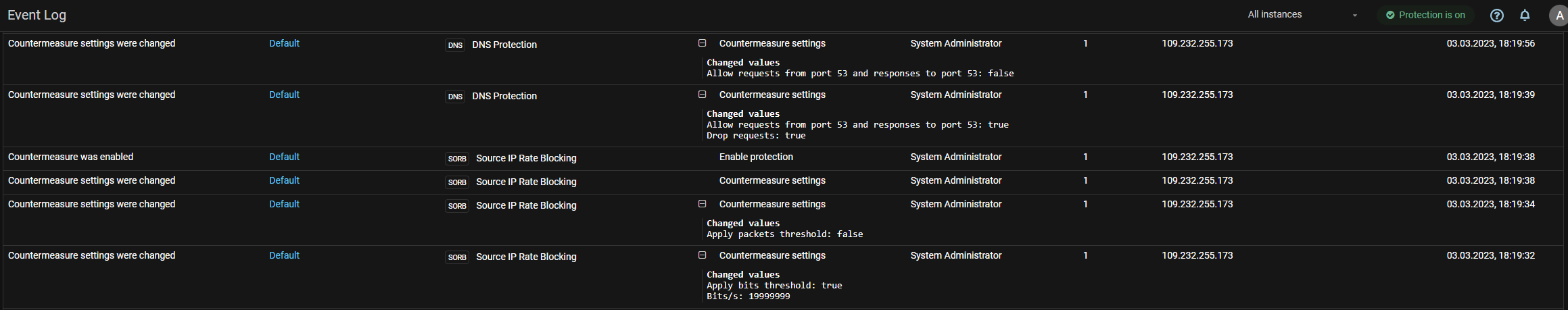
EventLog. Logging of countermeasure parameters being changed has been added in the event log.
Now, when changes to countermeasure settings are made, the changed values are displayed in the “Details” field of the event log.